Top InfoSec Innovator for SaaS Security Posture Management (SSPM)


CheckRed Editorial
Traditional defenses like firewalls and antivirus technologies struggle to keep up with the rate of emerging threats in the rapidly evolving digital world. It is here that context-aware security emerges as a transformative force. Gartner foresaw its rise as a critical solution for companies looking to modernize their security strategy as far back as 2012. Moreover, the exponential growth of cloud computing and security for SaaS applications has made it necessary for organizations to incorporate contextual information into their security decisions.
What is Context-aware Security?
Gartner defines context-aware security as ” the use of supplemental information to improve security decisions at the time they are made, resulting in more accurate security decisions capable of supporting dynamic business and IT environments.”
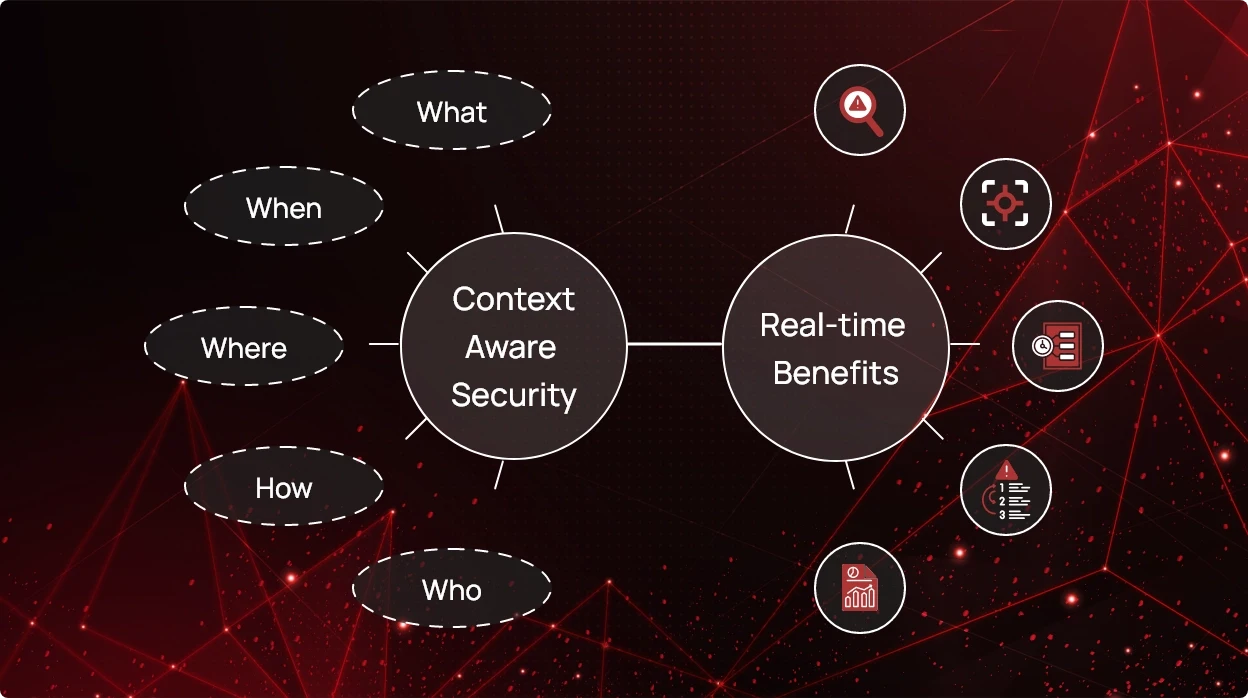
While environmental cues like location and time are commonly highlighted, valuable context spans the IT spectrum — encompassing IP, device, application information, and prevailing security risk context. Beyond data safeguarding, this approach sharpens security judgments by infusing decision moments with supplementary insights. A comprehensive solution attuned to the “when,” “where,” “how,” and “who” of each event easily helps improve security posture.
Security posture management tools like CheckRed play a vital role in bringing the concept of context-aware security to life. They delve deep into the security fabric, providing insights that are as varied as they are valuable. By deciphering intricate patterns and relationships, these tools empower organizations to craft robust security strategies. They offer a panoramic view of the security landscape, enabling swift responses to emerging threats.
Security posture solutions maintain an up-to-date and real-time record of devices, SaaS applications, cloud and network resources. This insight is indispensable for understanding what requires safeguarding and pinpointing potential weak spots. Moreover, these tools conduct regular risk assessments, meticulously scanning for known misconfigurations. By continuously monitoring the SaaS and cloud terrain, they ensure potential security issues are identified and addressed promptly.
Ensuring the integrity of applications and cloud systems is paramount, and security tools excel in this realm. They track the status of software patches and updates, acting as a shield against exploitation. Furthermore, these tools play a pivotal role in helping you enforce security configurations that align with best practices and compliance requirements. By setting and maintaining these configurations, they contribute significantly to the organization’s overall resilience.
Security posture platforms continuously assess security controls and configurations, ensuring all regulations, standards, and protocols are adhered to. They seamlessly integrate with risk intelligence feeds, offering real-time reports on emerging potential threats. This fusion of insights equips organizations to stay vigilant and respond effectively to potential risks.
The security tools gather and analyze data, assigning precise risk scores to assets and configurations. In times of security breaches, prioritizing risks with real-time context ensures proper resource allocation. Guided remediation workflows provide further assistance in mitigating these risks.
Security posture management tools offer more than insights; they transform data into meaningful reports. These intuitive representations enable quick comprehension of an organization’s security posture. Moreover, platforms like CheckRed seamlessly integrate with communication tools, creating a holistic shield against threats. This comprehensive approach empowers organizations to tackle multifaceted challenges with confidence.
Context-aware security is a significant strategy for all organizations operating in the cloud. Its adaptability and real-time benefits underscore its vital role in protecting sensitive data. Security posture management tools amplify this concept, offering insights that enhance an organization’s defensive strategies. CheckRed is a comprehensive SaaS and cloud security posture management solution that delivers the contextual information needed by security and compliance professionals.
Dive into the future with our interactive demo
and explore the possibilities.
Related Posts