Protect Your Microsoft 365 Environment with CheckRed
CheckRed protects Microsoft 365 by helping security teams harden configurations, manage access, detect excessive privileges, and quickly identify other security alerts.

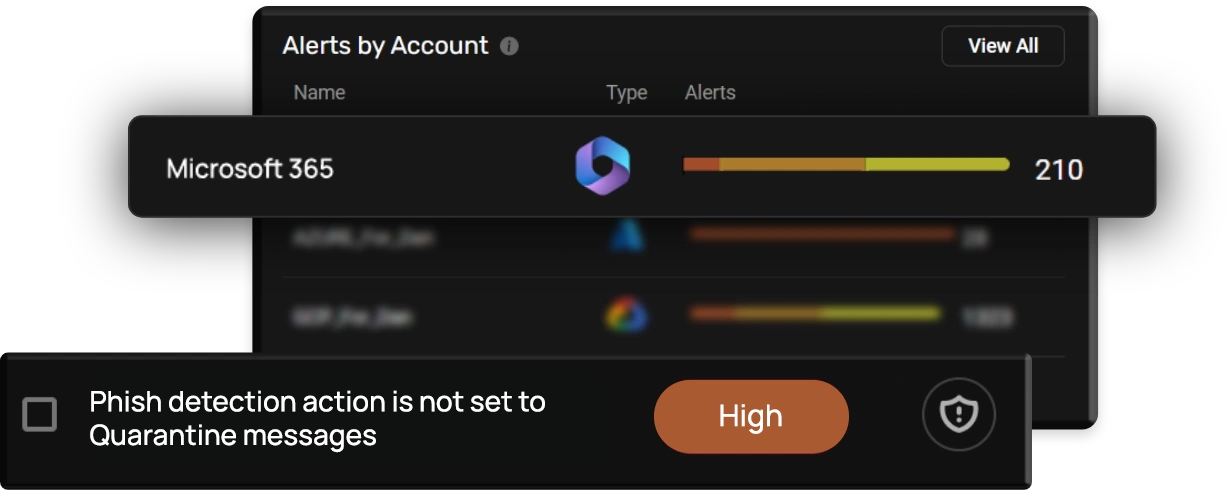
Securing Your Microsoft 365 Suite
Microsoft 365 is one of the most widely used business applications for organizations worldwide. It handles critical business data, including sensitive emails and files, which makes it vulnerable to attacks, threats, and accidental exposure. Each application has separate authorization protocols and internal & external settings that need to be continuously monitored. CheckRed ensures simplified security of Microsoft 365 by scanning the entire suite and automatically identifying risks.
Complete SaaS Security for Microsoft 365
Are You Aware of Your Microsoft 365 Security Risks?
Misconfigured Security Settings
Microsoft 365 apps have hundreds of security settings, requiring frequent updates to user privileges. Improper configurations can lead to data leaks and security gaps.
Third-Party Access Risks
Vendors with access to Microsoft 365 can be a weak link, increasing the risk of unauthorized access and account compromise.
Complex Compliance Requirements
Meeting industry security standards and generating compliance reports can be time-consuming and challenging without automation.
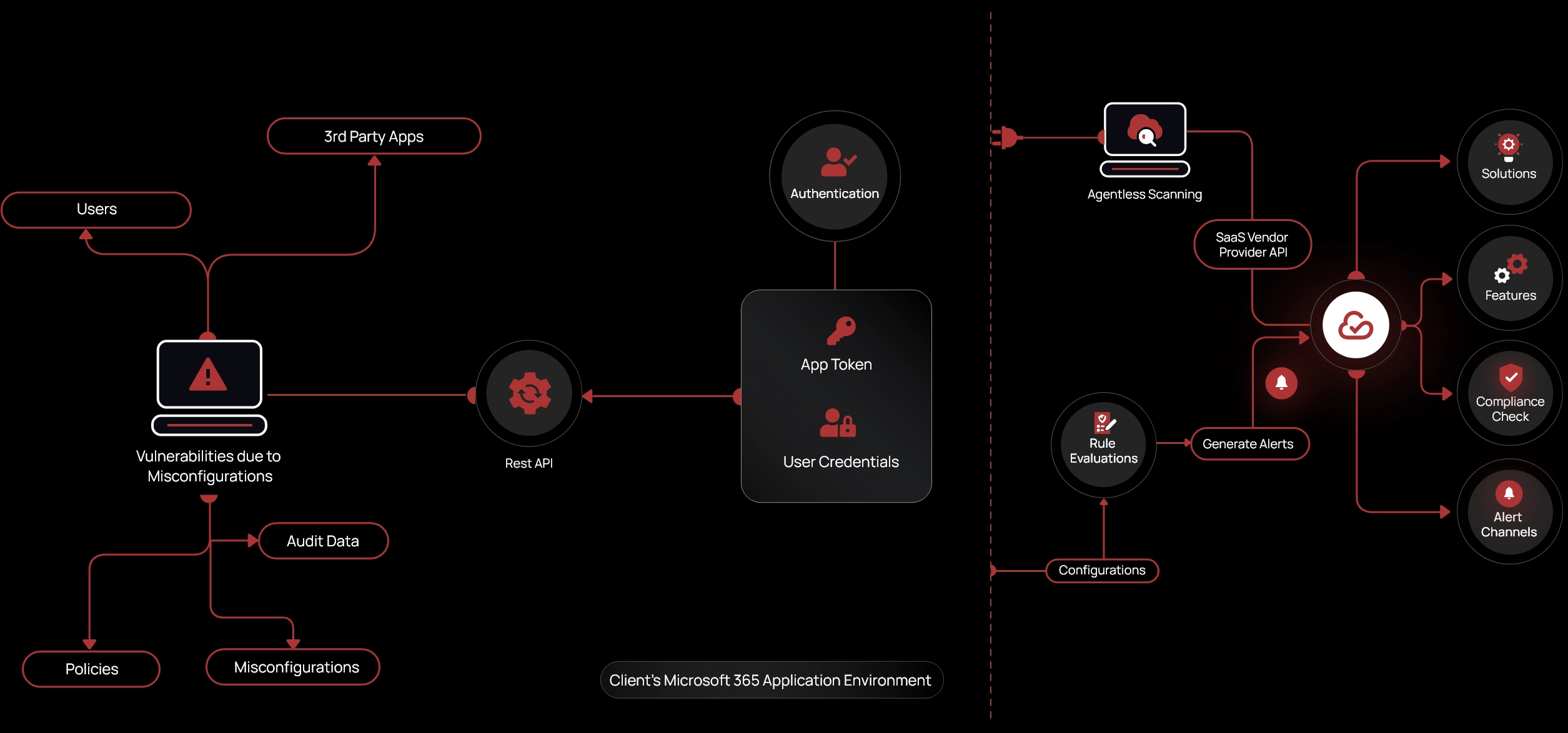
The CheckRed Approach
Inspect Microsoft 365 Applications
- Secure the Microsoft 365 environment with a combined set of controls
- Uncover risks and misconfigurations to gain deeper visibility with agentless scanners
- Audit internal and external user access and permission levels across applications
Detect Risks with Accuracy
- Identify misconfigurations, configuration drift, and unauthorized changes
- Gain real-time visibility into the Microsoft 365 environment with a single dashboard
- Use the customizable rule engine to monitor SaaS app activities and breaches
Prioritize & Focus on Key Misconfigurations
- Integrate automated alerts seamlessly and directly into the communication workflow
- Gain an at-a-glance view of all alerts and their classification based on severity
- Focus on high-severity alerts and trigger automated remediation workflows
Remediate with Customized Workflows
- Receive actionable alerts and personalized recommendations to accelerate fixes
- Track each alert from discovery to resolution through remediation workflows
- Monitor third-party applications and deliver remediation directly to users
Report with On-Demand Analytics
- Investigate and resolve issues with system-enabled creation and tracking of tickets
- Monitor and manage with a single dashboard and download customized reports
- Ensure compliance and standards are on par with industry best practices
Stay Ahead of Cyber Threats
Subscribe to our Monthly Cybersecurity Breakdown
Get the top cloud, SaaS, & DNS security insights delivered monthly—covering emerging threats, breaches, and cutting-edge strategies in one quick read.
Sign up now to stay informed, react faster, and strengthen security!
Frequently Asked Questions
What is SaaS Security Posture Management (SSPM) for Microsoft 365?
SSPM for Microsoft 365 helps organizations continuously monitor and secure their Microsoft 365 environments. It identifies security misconfigurations, monitors access privileges, and provides real-time visibility into user activity. SSPM ensures that security settings are properly managed, helping organizations prevent unauthorized access, data breaches, and compliance issues
How SSPM help prevent misconfigurations in Microsoft 365?
SSPM tools automatically scan Microsoft 365 configurations to detect misconfigurations or settings that could expose data to risks. By flagging potential issues such as unregulated access, third-party access vulnerabilities, or configuration drift, SSPM helps organizations correct these issues before they become security threats.
How does SSPM ensure compliance in Microsoft 365 environments?
SSPM helps organizations maintain compliance by continuously auditing Microsoft 365 against regulatory requirements and industry standards. It generates detailed compliance reports and alerts security teams on non-compliant configurations, ensuring that organizations can quickly address compliance gaps and meet audit requirements efficiently.