Prevent Ransomware with SaaS and Cloud Security
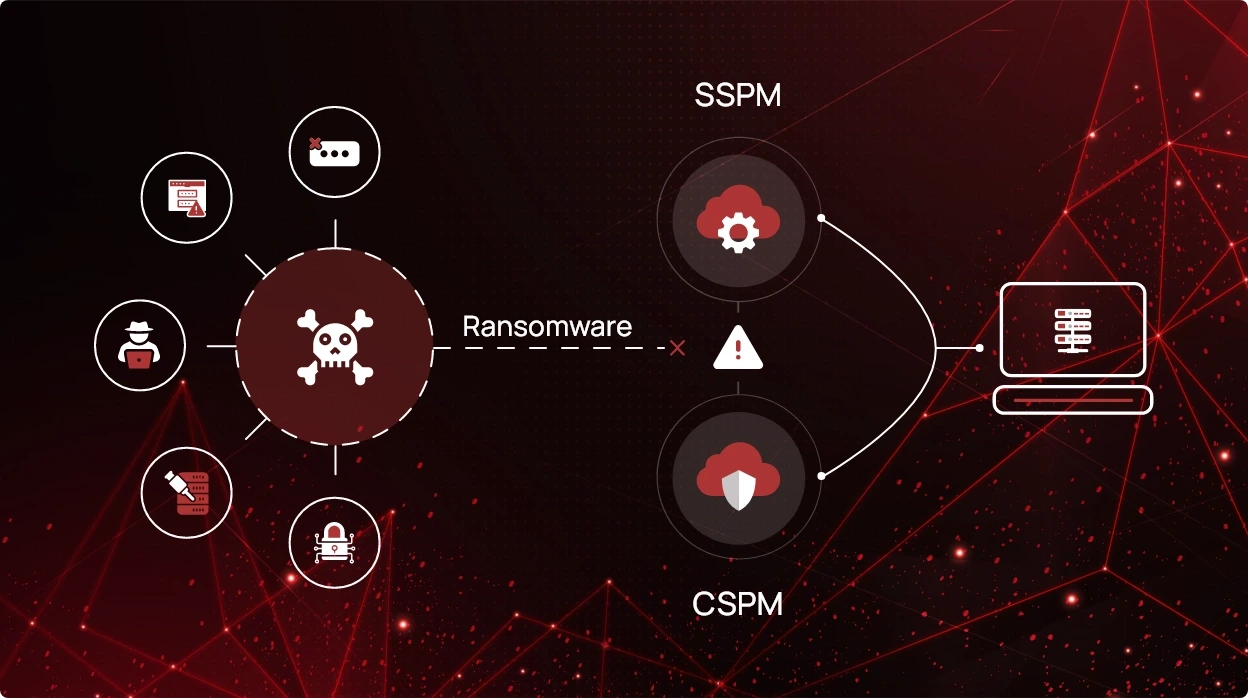
Ransomware poses a major threat to organizations worldwide. Hackers employ it to infect business systems, steal sensitive data, and encrypt vital information. This peril has grown more ominous with new tactics and the dark web’s involvement, granting hackers wider access. To safeguard against these attacks, businesses must enhance their SaaS and cloud security posture.
Understanding Ransomware
Ransomware is a type of malicious software that uses encryption to seize control of your data and demands payment to restore access. Unlike data breaches where information is stolen, ransomware locks you out of your own systems until a ransom is paid. This can cripple operations until access is regained.
Ransomware employs asymmetric encryption, requiring a unique pair of keys to unlock files. Attackers hold the private key, demanding payment for its release. Various ransomware types spread through email spam or targeted assaults, staying on systems until their task is done.
Once activated, ransomware searches for and encrypts valuable files, demanding payment within hours to unlock them. If backups are also compromised, victims have to pay the demanded ransom. Guarding against ransomware with proactive security measures is crucial to avoid falling victim to this devastating attack.
Ramifications of Ransomware Attacks
Ransomware attacks, like stealthy predators, can pounce on businesses, leaving a trail of havoc in their wake. The financial toll can be staggering—ranging from the hefty ransom demanded by attackers to potential long-term losses caused by disrupted operations. Organizations faced with the daunting choice of paying the ransom often grapple with moral and financial dilemmas.
Beyond the financial realm, a ransomware attack’s repercussions stretch to the core of a business’s reputation and customer trust. News of a breach spreads swiftly, eroding customer confidence and tarnishing the hard-earned reputation that took years to build.
Operational disruptions and downtime amplify the chaos, stalling productivity and impeding vital services. This grinding halt can reverberate across supply chains and impact partners and clients alike. The ripple effect of one attack can be felt far and wide.
Legal and regulatory consequences further compound the damage. Non-compliance with data protection regulations can lead to hefty fines, adding a legal quagmire to the already dire situation. The implications of a single ransomware breach can cascade into a spiral of financial, reputational, and legal woes.
In this landscape of escalating cyber threats, safeguarding against ransomware has become paramount. A proactive stance, fortified by security measures and cloud-based solutions, offers the best line of defense. The next sections delve into these proactive measures and the transformative role of application security posture management tools in bolstering resilience within SaaS applications and cloud environments.
Proactive Security Measures – Prevention is Better than Cure
Ransomware has become not just an occasional threat, but a consistent menace that targets organizations across the board. The alarming frequency of these attacks highlights the vulnerability of businesses in today’s interconnected world.
While responding to incidents remains vital, the focus is shifting toward prevention, a stance that carries greater weight in the fight against ransomware. Effectively thwarting ransomware requires a multi-pronged approach that starts from within.
- Regular employee training and awareness serve as the initial line of defense. Educating staff about phishing scams, malicious links, and suspicious attachments empowers them to identify potential threats.
- Robust data protection and recovery strategies are akin to a safety net. If vital data is properly backed up to offline or cloud-based repositories regularly, it will ensure that even if ransomware strikes, data can be restored without succumbing to ransom demands.
- Implementing multi-factor authentication (MFA) as well as identity and access management (IAM) adds an extra layer of security. Requiring users to provide multiple verification factors significantly reduces unauthorized access attempts.
- Keeping software and systems up to date might seem basic, yet it’s often overlooked. Regularly patching vulnerabilities closes entry points that ransomware exploits.
By adopting proactive measures, organizations reduce their exposure, stopping adversaries before they breach defenses.
Role of Security Posture Management Tools
SaaS Security Posture Management (SSPM) and Cloud Security Posture Management (CSPM) tools like CheckRed are pivotal in modern cybersecurity. They offer a comprehensive approach to risk mitigation, ensuring fortified SaaS applications and cloud environments.
- Real-time monitoring and incident response: CheckRed provides real-time monitoring, promptly alerting SOC analysts to potential security risks.
- Risk assessment: SSPM and CSPM tools like CheckRed conduct thorough risk assessments, pinpointing misconfigurations that might be exploited.
Benefits of SSPM and CSPM Tools in Preventing Ransomware
- Proactive risk identification and mitigation: CheckRed enables proactive risk identification, allowing organizations to foresee potential attack vectors. By preemptively addressing these risks, the likelihood of successful ransomware attacks diminishes.
- Continuous compliance monitoring: Compliance with industry regulations is crucial. These tools provide continuous compliance monitoring, alerting organizations to any deviations. Maintaining compliance not only safeguards against fines but also aligns security practices with industry standards.
SSPM and CSPM tools empower organizations to safeguard data, operations, and reputation effectively. Incorporating CheckRed into your security framework transforms your stance from reactive to proactive, effectively minimizing the potential for ransomware breaches.