Cloud Security for Amazon Web Services (AWS)
Protect & Strengthen Your AWS Cloud Environment with CheckRed
Managing AWS cloud security requires continuous monitoring, misconfiguration management, and proactive compliance monitoring. CheckRed’s advanced security platform delivers real-time risk detection, automated remediation, and full visibility, helping enterprises secure AWS workloads, prevent misconfigurations, and maintain compliance effortlessly.

Why Choose CheckRed for AWS Cloud Security?
- Complete AWS Visibility – Continuously monitor all AWS cloud assets for risks and compliance gaps.
- Automated Compliance & Risk Management – Meet security frameworks like GDPR, SOC 2, and NIST.
- Intelligent Risk Prioritization – Contextual security insights help teams address critical risks first.
- Seamless Security Collaboration – Integrate real-time alerts with Slack, Jira, and other tools.
Secure Your AWS Cloud & Prevent Misconfigurations
Gain Full AWS Cloud Visibility
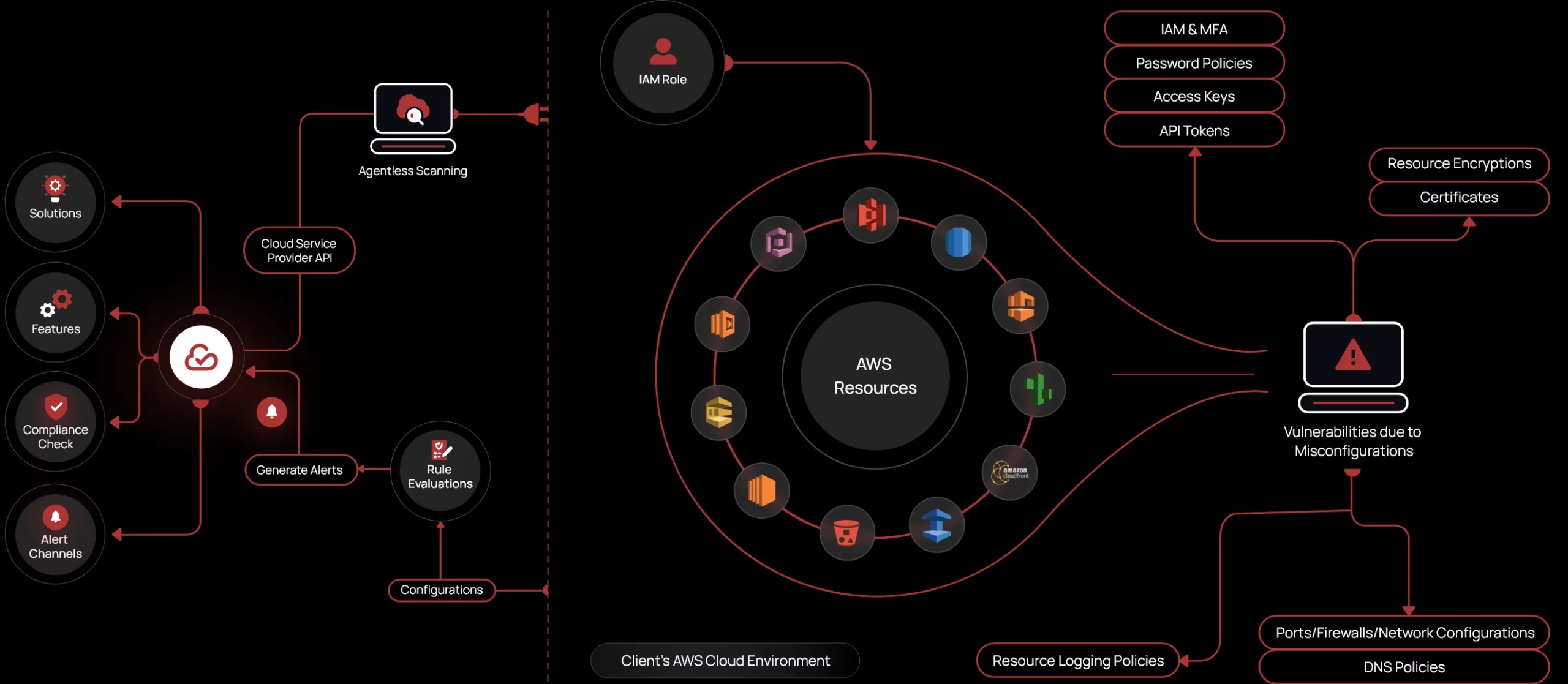
CheckRed’s agentless platform continuously scans AWS environments, identifying security risks without impacting performance.
Rapidly Detect & Resolve Security Issues
CheckRed deploys in minutes, scanning & detecting any risks in AWS cloud.
Automate Compliance & Security Readiness
Ensure compliance with customizable frameworks, automated audits, & real-time monitoring.
Actionable Risk Insights
CheckRed analyzes AWS configurations, permissions, & activity logs, delivering real-time alerts & risk categorization to prevent breaches.
Managing Your AWS Cloud Comes with Many Challenges
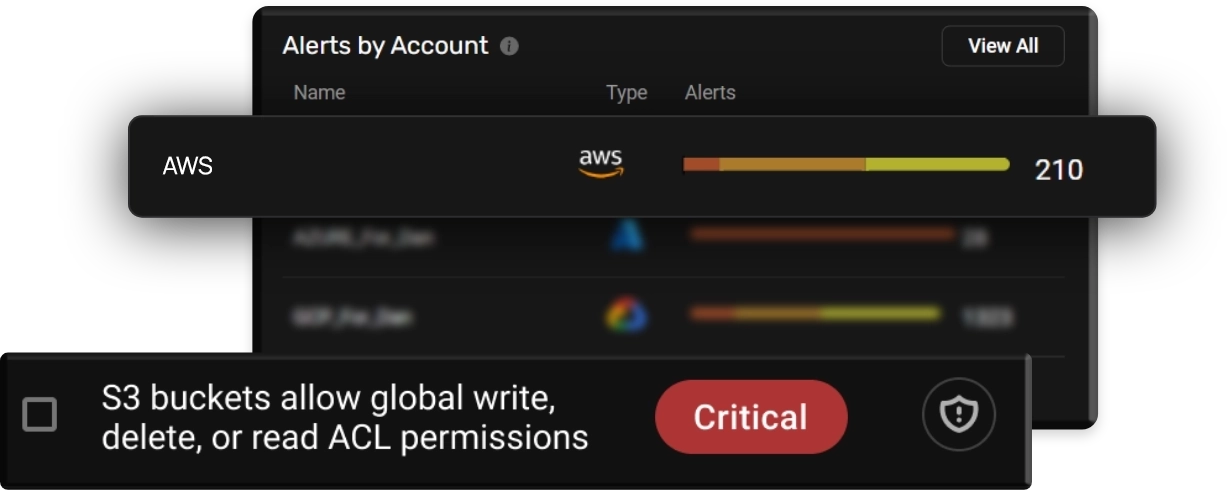
Unauthorized Usage of AWS S3 Buckets
Public exposure of your resources within AWS S3 buckets makes your critical business data susceptible to data leaks, manipulation and compliance violations.
Excessive Permissions in AWS Managed Policies
Undetected misconfigurations and irregular activity within your AWS Identity resources can lead to unauthorized access or excessive permissions.
Managing Privilege with AWS Identity Federation
AWS Identity Federation introduces security and compliance complexities, requiring continuous monitoring to enforce least privilege access.
An Innovative Approach to AWS Cloud Security
Total Visibility
With CheckRed, enterprises can gain comprehensive visibility of their AWS cloud. Our agentless platform audits and captures any risk without impacting organizational performance.
Contextual Alerts
CheckRed analyzes AWS cloud assets and provides actionable information by categorizing and prioritizing risks. Address critical issues in real-time and prevent security breaches.
Remediation Workflows
The AWS cloud functions at its best when it is secure. CheckRed generates automated and semi-automated remediation workflows, custom rules, and reports for optimal performance.
Frequently Asked Questions
What is Cloud Security Posture Management (CSPM) for AWS?
CSPM for AWS refers to a specialized security tool designed to manage and enhance the security configurations of AWS cloud environments. CSPM helps businesses ensure that their AWS cloud settings align with security best practices and regulatory requirements, reducing the risk of data breaches and improving overall cloud security posture through continuous monitoring and automated remediation features.
Why is visibility important in AWS cloud security?
Visibility into AWS assets and configurations is necessary for identifying risks and preventing data breaches. AWS environments are highly dynamic, with new services, permissions, and data constantly changing. Without total visibility, security teams may miss misconfigurations, unauthorized access, or excessive privileges, leading to compliance failures and vulnerabilities.
How does automation improve cloud security in AWS?
Automated tools streamline the detection and remediation of security risks in AWS by applying real-time monitoring, prioritizing alerts based on risk, and generating automated remediation workflows. As a result, it reduces the workload on security teams and ensures quicker responses to potential threats. The automation tools also enhance security response times and reduce the need for manual oversight.
Stay Ahead of Cyber Threats
Subscribe to our Monthly Cybersecurity Breakdown
Get the top cloud, SaaS, & DNS security insights delivered monthly—covering emerging threats, breaches, and cutting-edge strategies in one quick read.
Sign up now to stay informed, react faster, and strengthen security!