Comprehensive Cloud Security for Microsoft Azure
End-to-End Protection for Your Azure Cloud Environment
Enterprises migrate to Microsoft Azure for its flexibility, scalability, and performance, but securing Azure requires more than outdated, multi-tool security approaches. CheckRed delivers an all-in-one cloud security platform that ensures continuous protection, compliance, and risk remediation for your Azure environment.

Why Choose CheckRed for Microsoft Azure Security?
- Complete Visibility & Control – Monitor all Azure cloud assets in real time.
- Automated Risk Detection & Remediation – Identify and fix misconfigurations fast.
- Continuous Compliance Management – Meet regulatory standards effortlessly.
- Seamless Collaboration – Integrate alerts with Slack, Jira, and more.
Addressing the Biggest Azure Security Challenges
Prevent Unauthorized Access
Misconfigured access keys can lead to excessive permissions and security vulnerabilities. CheckRed automatically detects and mitigates these risks.
Strengthen Identity & Access Management (IAM)
Azure IAM misconfigurations can go unnoticed, leading to unauthorized access. CheckRed continuously monitors permissions and alerts you to anomalies.
Overcome Native Security Limitations
Azure’s built-in security tools lack the granularity needed to detect all misconfigurations and governance risks. CheckRed provides advanced risk detection and proactive security enforcement.
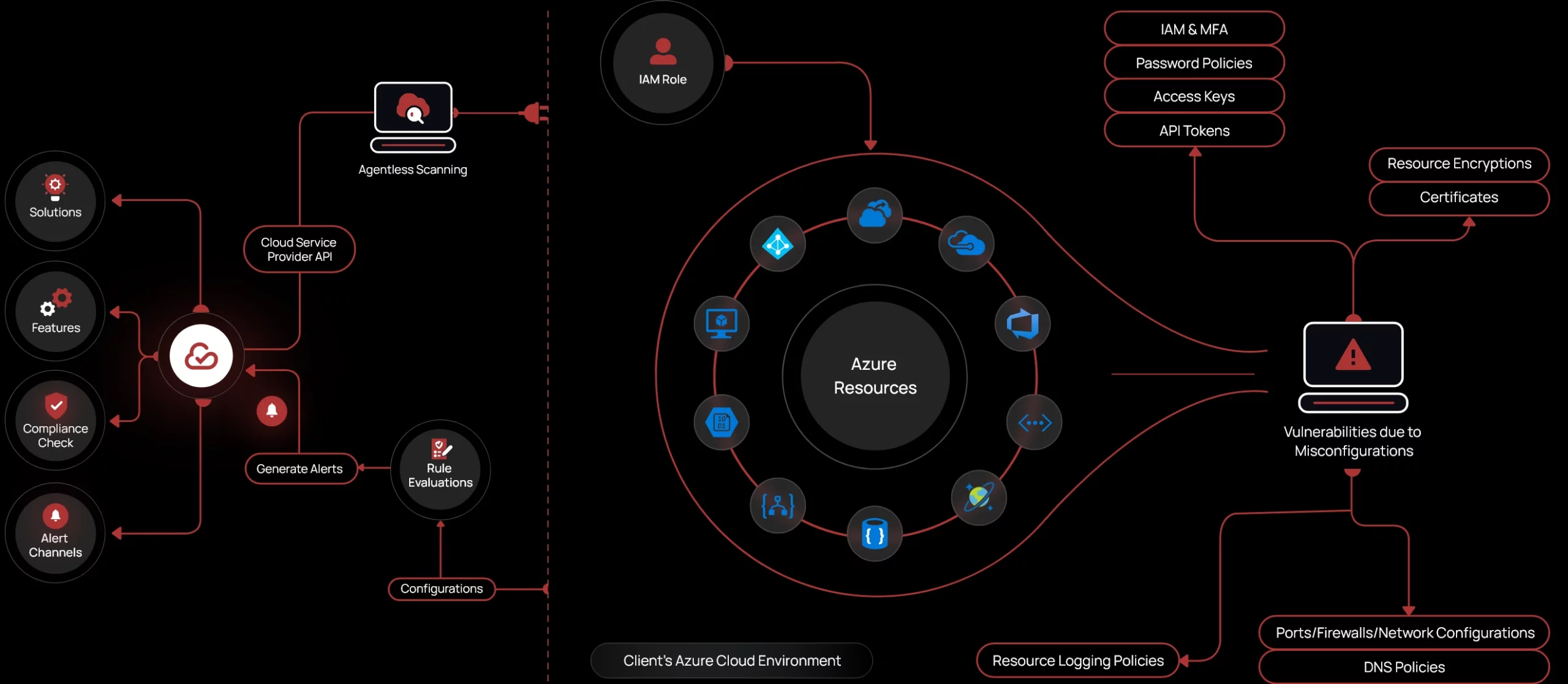
A Unified Cloud Security Platform for Azure
Real-Time Risk Detection
CheckRed continuously scans your Azure environment, identifying misconfigurations, IAM risks, unsecured data, and anomalies within minutes.
Customizable Rules Engine
Use built-in security templates, compliance frameworks, and automated rules, or customize them to fit your enterprise’s unique needs.
Context-Rich Insights
CheckRed’s agentless scanning rapidly evaluates security risks based on severity, providing actionable intelligence to prevent breaches before they happen.
Eliminate Security Gaps in Your Azure Environment
Secure Azure Cloud, End to End
Ensure your Azure cloud environment is protected with continuous monitoring and automated security enforcement.
Simplify & Prove Compliance
Use built-in and customizable compliance frameworks to identify and fix security gaps before they become threats.
Get Actionable, Context-Rich Reports
Stay ahead of breaches with AI-powered risk categorization and insightful security analytics.
Eliminate Communication Silos
Receive real-time alerts via Slack, Jira, or other collaboration tools, keeping teams aligned and informed.
Frequently Asked Questions
What is Cloud Security Posture Management (CSPM) for Azure?
CSPM for Microsoft Azure is a security solution that monitors, detects, and remediates misconfigurations, compliance violations, and security risks across cloud assets. It helps enterprises maintain regulatory compliance, secure sensitive data, and protect against vulnerabilities.
How does CSPM help ensure compliance in Azure environments?
CSPM tools play a vital role in maintaining compliance in Azure by continuously auditing the cloud environment against industry standards and regulatory requirements. They help organizations adhere to frameworks like GDPR, SOC 2, HIPAA, and ISO by identifying non-compliant configurations and generating detailed compliance reports. CSPM ensures that organizations can quickly address compliance issues and demonstrate adherence during audits, significantly reducing the risk of penalties or data breaches associated with non-compliance.
How do automation remediation features benefit Azure cloud security?
Automated remediation in Azure cloud security minimizes the risk of human error and accelerates the process of fixing security vulnerabilities. When misconfigurations or threats are detected, automated tools can instantly apply predefined fixes, such as adjusting firewall rules or revoking unnecessary permissions. Automated remediation also reduces the burden on security teams, allowing them to focus on higher-priority tasks.
Stay Ahead of Cyber Threats
Subscribe to our Monthly Cybersecurity Breakdown
Get the top cloud, SaaS, & DNS security insights delivered monthly—covering emerging threats, breaches, and cutting-edge strategies in one quick read.
Sign up now to stay informed, react faster, and strengthen security!