Comprehensive Google Cloud Security with CheckRed
Strengthen Your Google Cloud Security Posture
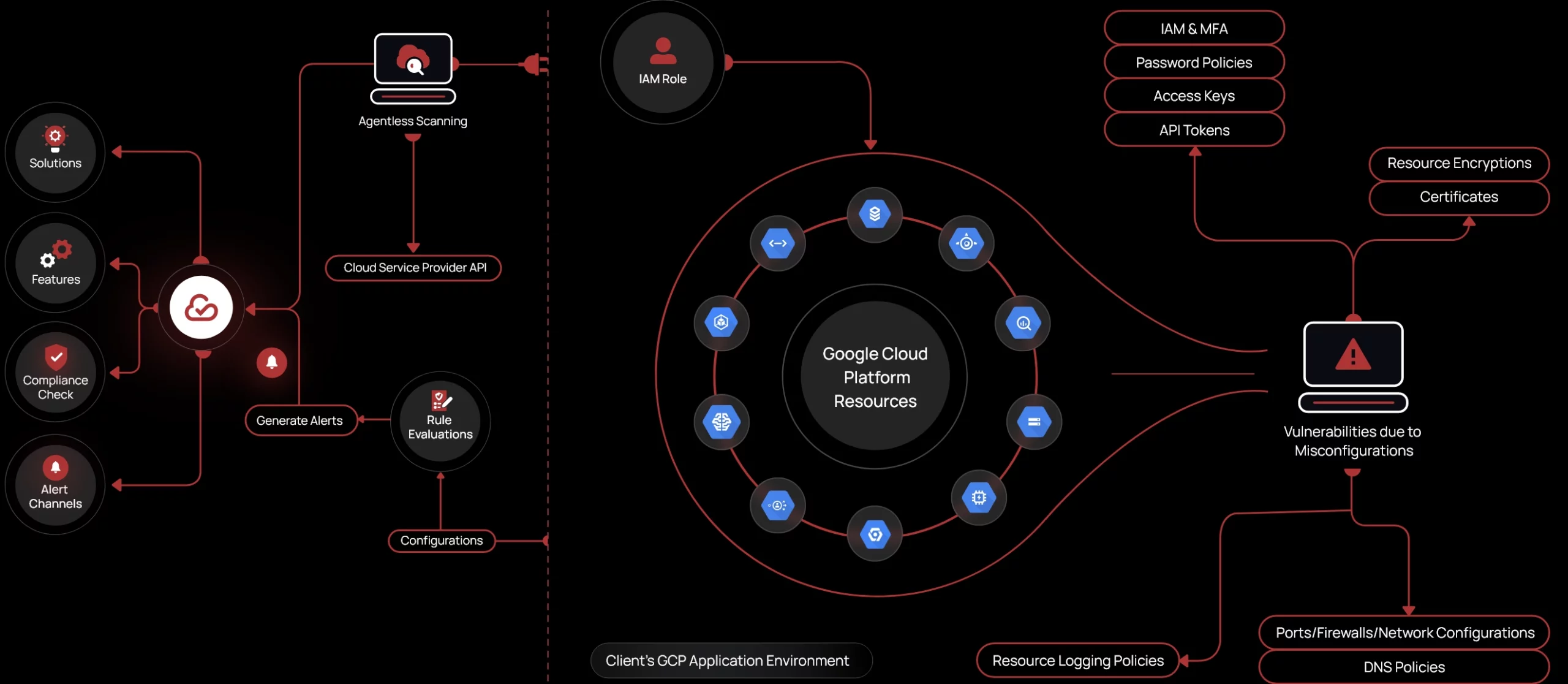
Google Cloud Platform (GCP) offers scalability and flexibility, but securing cloud resources requires continuous monitoring and proactive risk management. CheckRed’s cloud security platform provides real-time threat detection, automated remediation, and continuous compliance monitoring, ensuring enterprises, MSPs, and MSSPs can confidently secure their Google Cloud environment.


Why Choose CheckRed for Google Cloud Security?
- Full Visibility & Control – Monitor all Google Cloud assets in real-time
- Automated Risk Detection & Remediation – Identify and fix misconfigurations instantly
- Continuous Compliance Monitoring – Meet regulatory requirements effortlessly
- Seamless Integration & Collaboration – Get alerts directly in Slack, Jira, and more
Effortlessly Protect Your Google Cloud Environment
Detect Anomalies & Misconfigurations
CheckRed automates risk detection, helping security teams focus on critical threats first.
Improve Security Posture with Contextual Insights
CheckRed analyzes every Google Cloud asset, providing actionable insights to proactively mitigate risks.
Maintain Compliance with Confidence
Meet industry regulations with continuous compliance monitoring and customizable security frameworks.
Streamline Security Operations
Obtain alerts seamlessly on collaboration tools like Slack or Jira with CheckRed’s integrations.
Are Your Google Cloud Resources Fully Secure?
Google Cloud Platform’s Basic Roles Create Security Risks
Granting broad user permissions in Google Cloud can lead to public data exposure and unnecessary access privileges.
Third-Party Access Increases Security Vulnerabilities
Unmonitored third-party access to Google Cloud resources can introduce data breaches and compliance risks.
Google’s Managed Service Accounts can be Exploited
Without advanced security controls, sensitive information managed by GCP’s service accounts could be exposed.
A Smarter Approach to Google Cloud Security
Complete Security Coverage
CheckRed’s agentless scanners monitor every Google Cloud asset and provide full visibility without impacting performance.
Automated Risk Alerts & Threat Detection
Receive real-time security alerts, allowing enterprises, MSPs, and MSSPs to remediate high-risk issues immediately.
Data-Driven Remediation Workflows
CheckRed delivers automated and semi-automated remediation workflows based on comprehensive security risk analysis, ensuring a proactive security approach.
Frequently Asked Questions
What is Cloud Security Posture Management (CSPM) for Google Cloud?
CSPM for Google Cloud is a security solution that monitors and audits cloud configurations to detect misconfigurations, vulnerabilities, and compliance risks. It ensures continuous visibility, aligns security settings with best practices, and automates threat detection and remediation to protect Google Cloud environments.
How does CSPM enhance data security in Google Cloud?
CSPM strengthens Google Cloud data security by continuously monitoring for risks, such as public data exposure, misconfigured permissions, and unauthorized access. It provides real-time alerts and automated remediation workflows, enabling enterprises to quickly address security gaps.
What role does CSPM play in ensuring compliance for Google Cloud?
CSPM tools are crucial for maintaining compliance in Google Cloud environments by auditing configurations against industry standards and regulatory frameworks. They provide continuous monitoring, generate compliance reports, and help security teams quickly identify and fix non-compliance issues. This reduces the risk of penalties and ensures that organizations meet legal and regulatory obligations while operating in the cloud.
Stay Ahead of Cyber Threats
Subscribe to our Monthly Cybersecurity Breakdown
Get the top cloud, SaaS, & DNS security insights delivered monthly—covering emerging threats, breaches, and cutting-edge strategies in one quick read.
Sign up now to stay informed, react faster, and strengthen security!