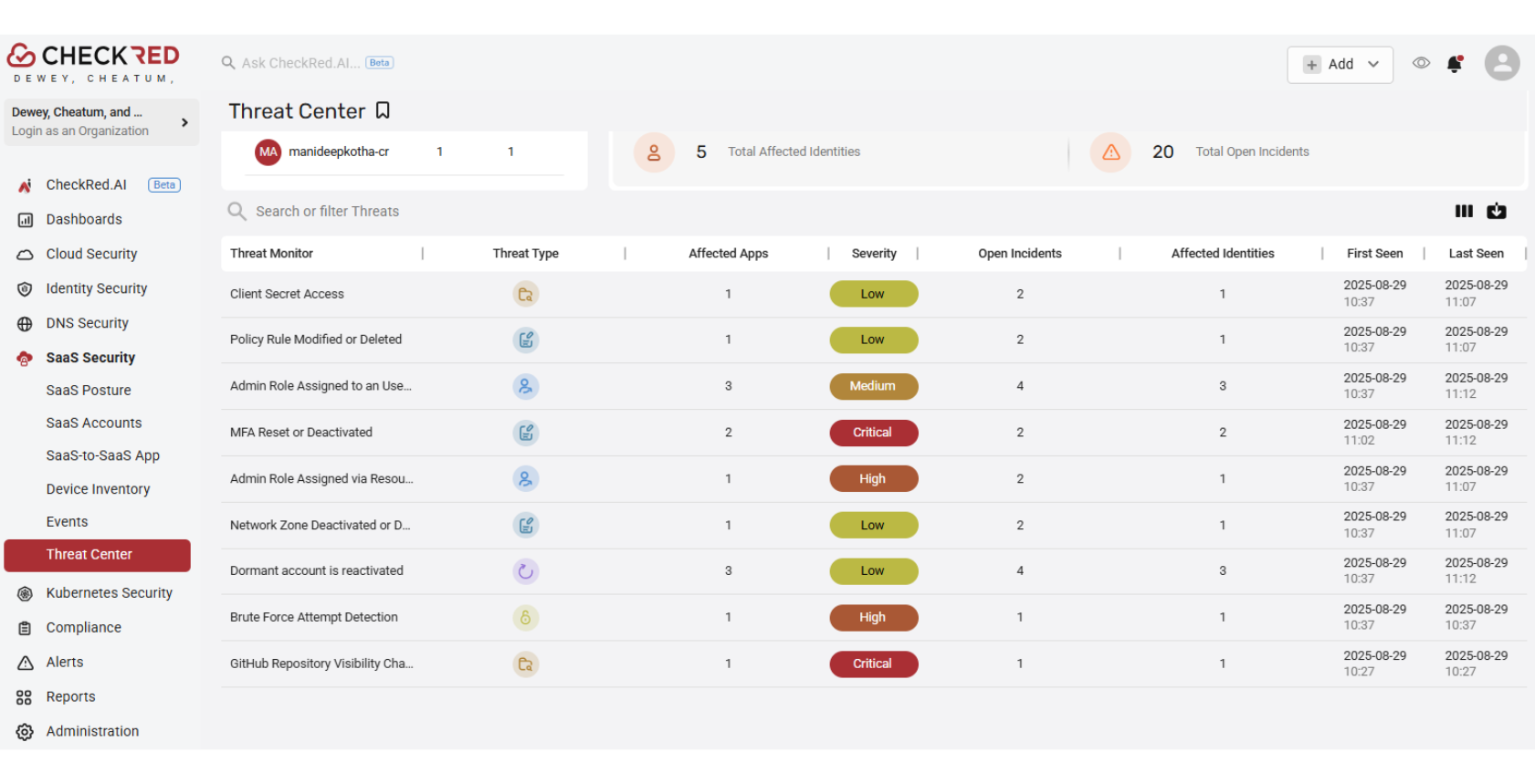
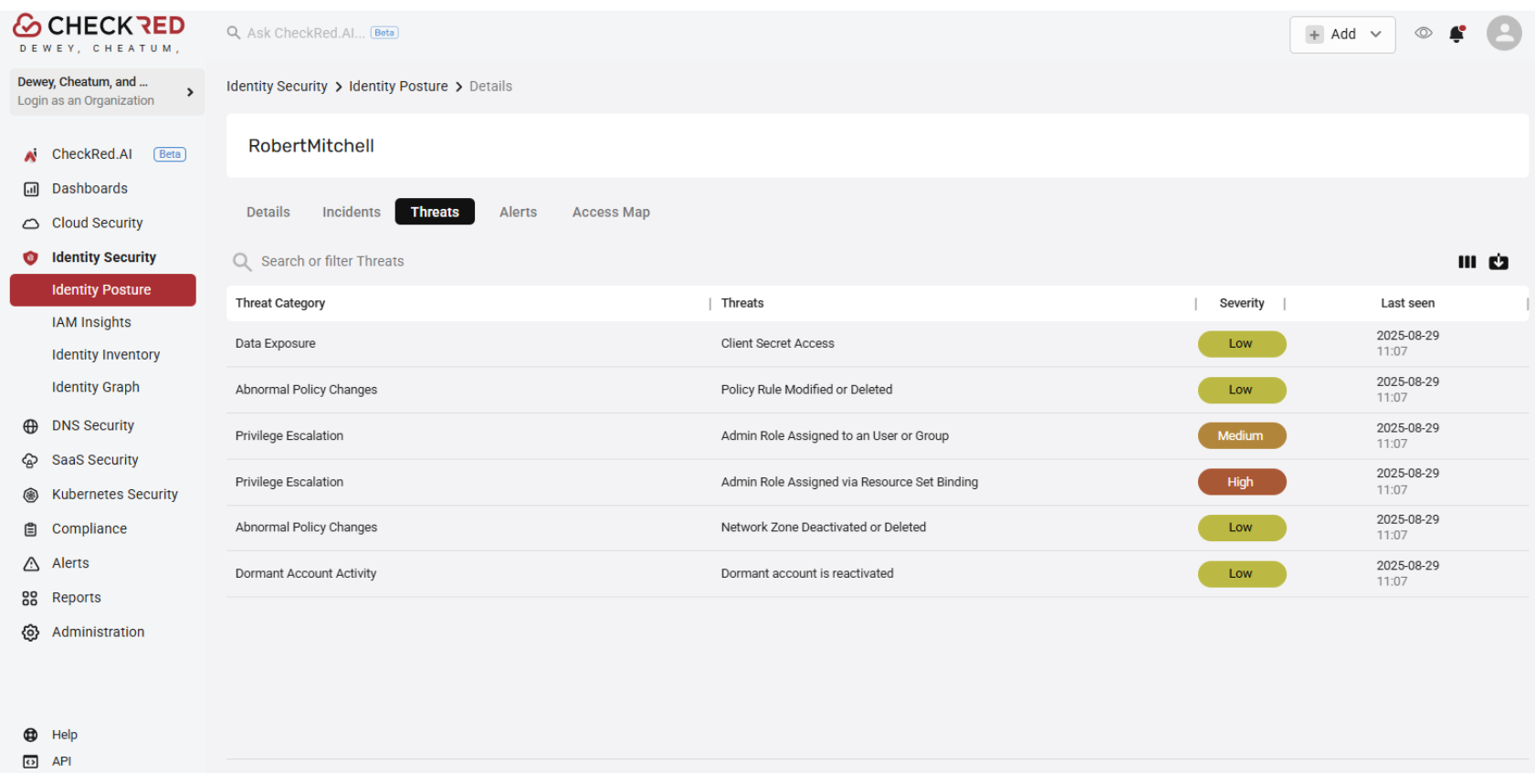
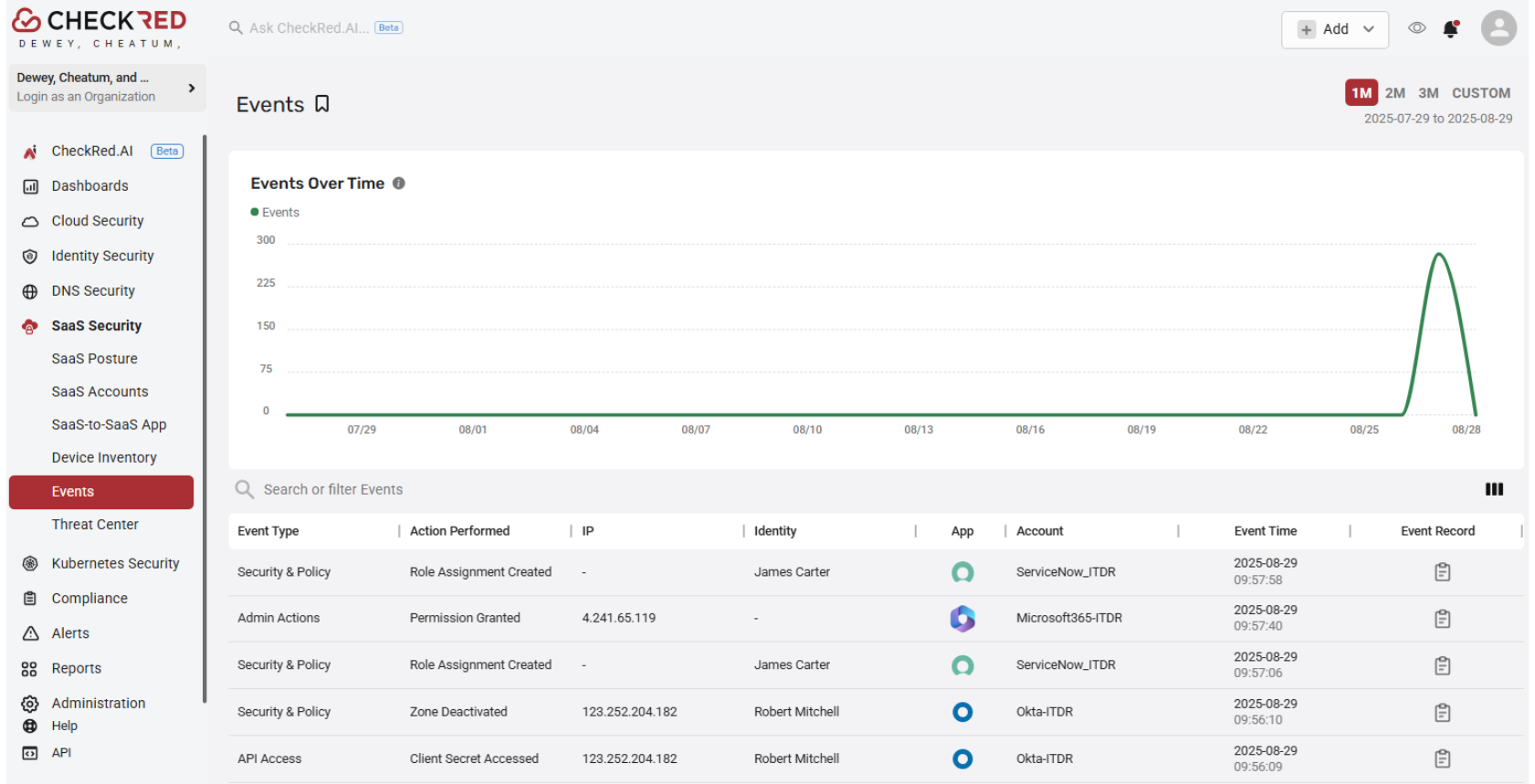
Identity Threat Detection & Response (ITDR)
Stop Identity-Based SaaS Threats Before They Escalate
Unmanaged identities, excessive permissions, and hidden misconfigurations make SaaS environments prime targets. One privilege escalation or hijacked session can expose your entire organization.
CheckRed ITDR delivers real-time visibility, AI-powered behavioral analytics, and automated response—built specifically to secure SaaS identities.
See Threats Before They Become Incidents
With CheckRed’s Identity Threat Detection & Response (ITDR), your security team can proactively detect, investigate, and respond to identity-based threats across your SaaS environment.
Real-time Threat Detection
Receive instant alerts for privilege escalation, dormant account reactivation, brute force attempts, and more.
Built-In Behavioral Analytics
Detect anomalous user behavior and deviations from baseline activity using machine learning.
24/7 SaaS Monitoring
Continuous monitoring and unified visibility across all SaaS apps—from login events to policy changes.
Identity-Centric Investigation
Map threats directly to impacted users with detailed profiles, permission tracking, and contextual insights.
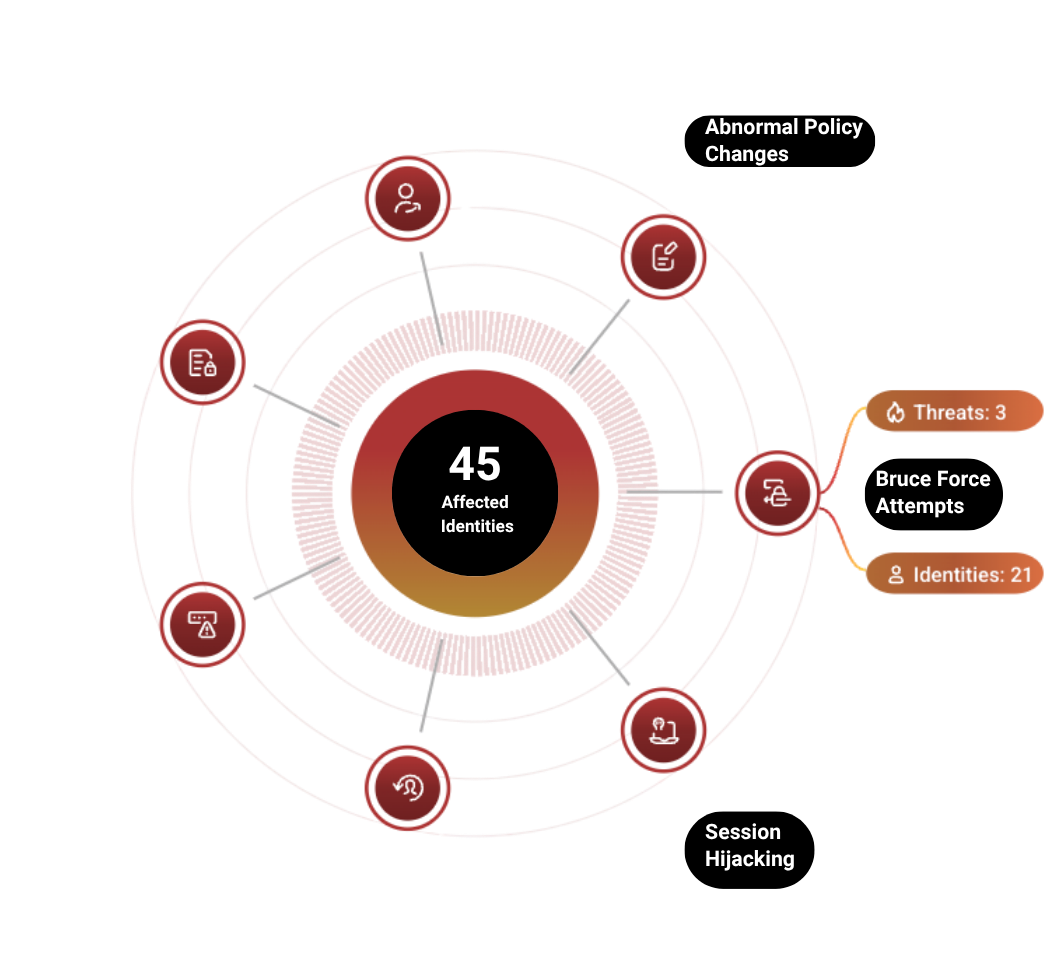
The 7 SaaS Identity Threats You Must Monitor
CheckRed’s ITDR engine continuously tracks and analyzes the top identity-based risks in your SaaS stack:
- Privilege Escalation – Unauthorized access level changes
- Anomalous Behavior – Deviations from normal user activity
- Abnormal Policy Changes – Unsanctioned changes to key security settings
- Session Hijacking – Token theft or location-based login anomalies
- Brute Force Attempts – Excessive failed login attempts
- Data Exposure – Unusual access to sensitive files
- Dormant Account Reactivation –Unexpected activity on inactive users

The CheckRed ITDR Advantage
CheckRed vs. the Competition
Other solutions focus on configurations. We focus on what matters now: live identity threats.

Frequently Asked Questions
What is Identity Threat Detection and Response (ITDR)?
ITDR is a security approach focused on detecting, analyzing, and responding to identity-based threats—like privilege escalation, session hijacking, and dormant account abuse—across SaaS environments. CheckRed ITDR provides real-time visibility and automated threat response, purpose-built for SaaS security.
How is CheckRed ITDR different from traditional SaaS security tools?
While many tools focus on configuration management or posture analysis, CheckRed goes deeper—tracking live identity activity, applying machine learning to detect anomalous behavior, and correlating threats across platforms for faster, smarter response.
Can CheckRed ITDR integrate with my existing security tools?
Yes. CheckRed ITDR is designed for seamless integration with your current security stack, including SIEM, SOAR, and collaboration tools, making it easy to streamline workflows and accelerate incident resolution.
Stay Ahead of Cyber Threats
Subscribe to our Monthly Cybersecurity Breakdown
Get the top cloud, SaaS, & DNS security insights delivered monthly—covering emerging threats, breaches, and cutting-edge strategies in one quick read.
Sign up now to stay informed, react faster, and strengthen security!