Protect Okta from Security Breaches
CheckRed protects Okta by identifying critical misconfigurations and monitoring for security breaches or behavioral anomalies.

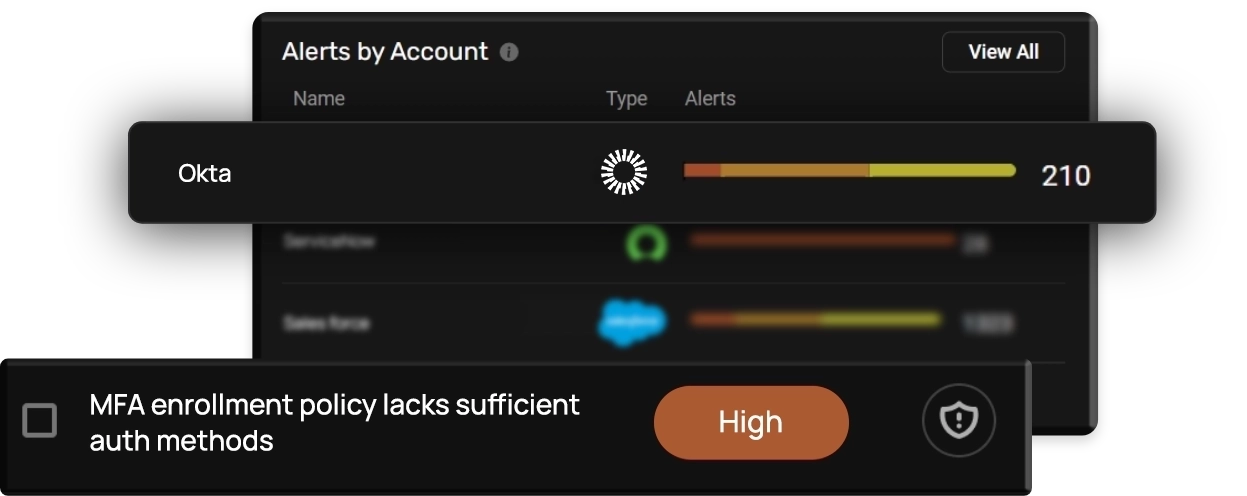
Enhance Okta’s Security Posture
As organizations scale, Identity and Access Management (IAM) solutions like Okta play a crucial role in securing authentication through Single Sign-On (SSO) and Multi-Factor Authentication (MFA). While Okta simplifies identity validation, misconfigurations, excessive permissions, and unauthorized access can expose sensitive data.
CheckRed enhances Okta’s security posture with real-time monitoring, risk detection, and automated remediation, ensuring secure access management and compliance.
Proactively Detect Risks in Okta
Are You Aware of Okta’s Security Challenges?
High Risk of Misconfigurations
Overlapping application assignments, privilege escalations, and excessive permissions increase security vulnerabilities.
Increased Access Exposure
With multiple employees, vendors, and third-party stakeholders, excessive access can lead to unauthorized exposure of sensitive assets.
Limited Visibility Across User Identities
Unlinked or duplicate identities across applications make user activity monitoring and threat detection difficult.
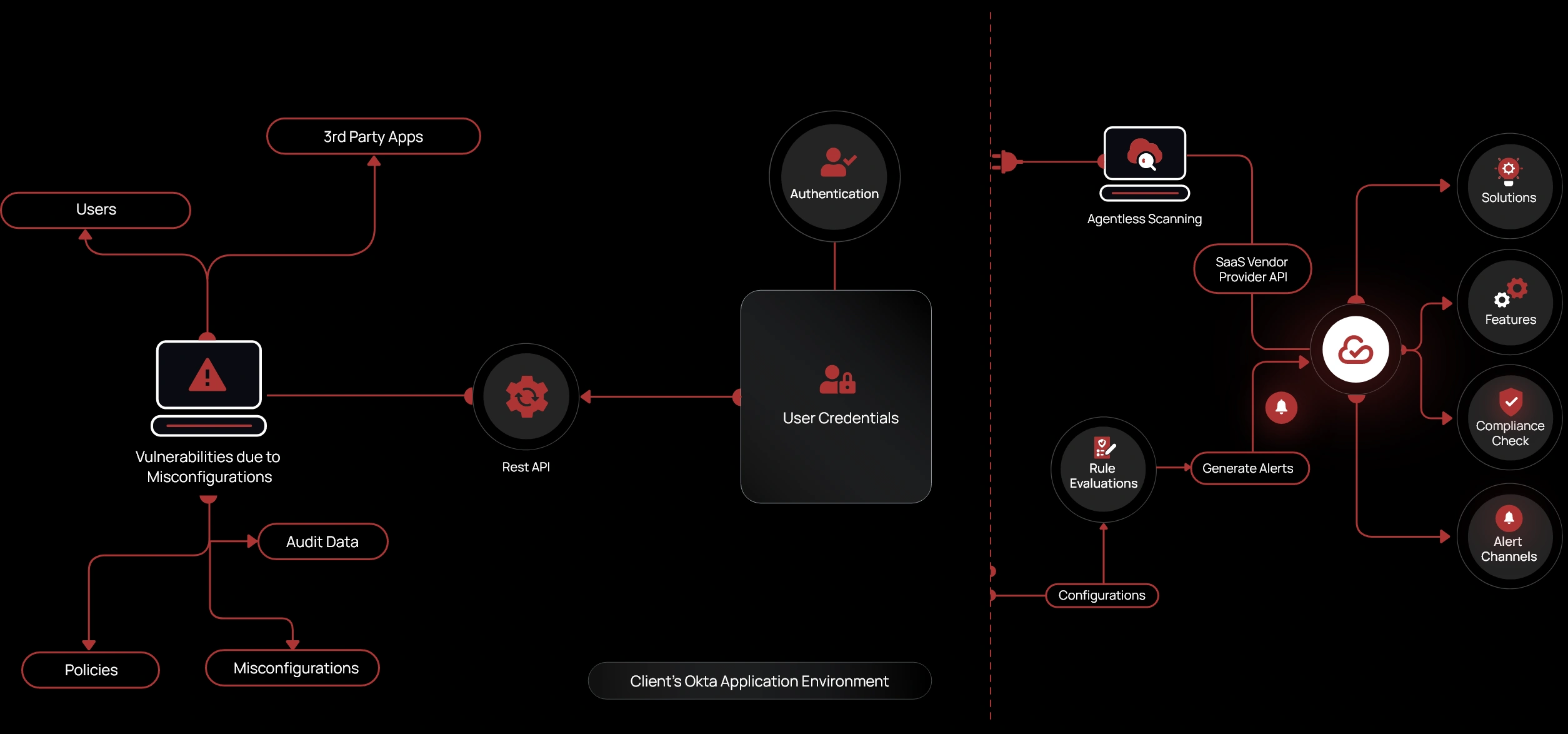
The CheckRed Approach
Inspect Okta
- Conduct agentless scanning for risks and vulnerabilities to acquire in-depth visibility
- Enhance the Okta environment with a diverse array of controls
- Assess internal and external user access and clearance levels across applications
Detect Risks with Accuracy
- Apply rule sets and templates to monitor application activities and breaches
- Detect misconfiguration, configuration drift, and unauthorized modifications
- Get real-time visibility into the Okta environment with a centralized dashboard
Prioritize & Focus on Critical Misconfigurations
- Effortlessly integrate automated notifications into the workflow
- View all alerts and their classification based on criticality and risk scoring in one place
- Focus on high-impact alerts and activate automated responses for common risks
Remediate with Customized Workflows
- Receive action-driven alerts and personalized suggestions to accelerate fixes
- Inspect third-party integrations and provide remediation directly to users
- Follow each alert from detection to resolution through remediation workflows
Report with On-Demand Analytics
- Ensure compliance and conformity to industry standards and best practices
- Get a full overview with a single dashboard and download customized reports
- Use actionable risk intelligence to empower your security and DevOps teams
Stay Ahead of Cyber Threats
Subscribe to our Monthly Cybersecurity Breakdown
Get the top cloud, SaaS, & DNS security insights delivered monthly—covering emerging threats, breaches, and cutting-edge strategies in one quick read.
Sign up now to stay informed, react faster, and strengthen security!
Frequently Asked Questions
What is SSPM for Okta?
SaaS Security Posture Management (SSPM) tools for Okta help to monitor and analyze the security of Okta’s identity and access management solutions. These tools enable organizations to assess the effectiveness of their security configurations, monitor user access privileges, and identify potential vulnerabilities within the Okta environment. They enhance security and improve operational efficiency by allowing organizations to respond proactively to security incidents and adapt their strategies as needed.
How does SSPM benefit organizations using Okta?
SaaS Security Posture Management (SSPM) provides organizations using Okta with the tools and frameworks to ensure that security policies are being enforced consistently and to adjust them as necessary. Additionally, SSPM facilitates proactive incident response by highlighting potential security risks within the Okta environment, allowing organizations to address vulnerabilities and enhance their overall security posture quickly.
How can SSPM improve compliance in Okta environments?
SSPM can significantly enhance compliance in Okta environments by providing comprehensive visibility into user access. SSPM tools help organizations ensure that their identity and access management policies align with regulatory requirements, such as GDPR, HIPAA, ISO, or SOC 2. They facilitate detailed reporting capabilities, making it easier to demonstrate compliance during assessments and audits.