2024: What is the cost of a data breach today?

While security and compliance teams are improving their ability to detect and respond to breaches, threat actors are causing increasingly severe financial damage to organizations as evident by the high number of cyberattacks recently. As cyber threats evolve and become more sophisticated, the cost of breaches is rising, impacting not just immediate financial losses but also long-term operational and reputational harm. The growing complexity of attacks means that even with advanced defenses, organizations must continually adapt and enhance their security strategies to mitigate these escalating risks.
The cost of a data breach
IBM recently released their 19th edition of the “Cost of a Data Breach” report, and the global average cost of a breach reached a new record high of $4.88 million. It increased by 10% since last year, reflecting not only the direct financial impact but also the growing complexity of breaches, which involve extensive remediation efforts, legal liabilities, and reputational damage. As attackers become more sophisticated, organizations must prioritize comprehensive security solutions and proactive risk management to safeguard against escalating threats and mitigate the financial repercussions of potential breaches.
Key insights on cloud and SaaS security from the report
Nearly half of all breaches involved data stored in multiple cloud environments
The report highlighted that about 40% of all data breaches involve information distributed across various environments, including public clouds, private clouds, and on-premises systems. This trend highlights a growing challenge for organizations as they grapple with securing increasingly dynamic and dispersed data.
The distribution of data across multiple environments complicates several critical security tasks. First, discovering and classifying data becomes more difficult when it resides in disparate clouds and SaaS applications. Traditional protection measures, which may have been effective in a more centralized environment, often struggle to keep pace with the fluid nature of data spread across multiple platforms. This dispersion can lead to gaps in visibility, making it challenging to identify where sensitive information resides, who has access to it, and how it’s being used.
Tracking data movement and access across different environments adds another layer of complexity. With data flowing between public and private clouds and on-premises systems, as well as between internal teams and external vendors, it becomes harder to monitor and control its usage effectively. This lack of centralized oversight can increase the risk of unauthorized access or data leaks.
How can you mitigate this? Securing data in such a distributed setup requires advanced solutions that can provide comprehensive visibility and control across all cloud and SaaS environments. Organizations need to implement strong cloud security strategies and employ technologies that offer unified security management. This includes tools that can track assets across clouds, enforce consistent security policies, and rapidly respond to potential threats. As cloud environments become more dynamic, maintaining effective security measures becomes crucial to protect against breaches and mitigate their impact.
Multi-environment breaches took the longest to remediate
IBM reported that “multi-environment breaches cost more than $5 million on average and took the longest to identify and contain (283 days).” Breaches involving data distributed across multiple environments – such as public clouds, private clouds, on-premises systems, and SaaS applications – are proving to be particularly costly and complex to manage. They incur high costs and require a long time to identify and contain. This extended timeframe underscores the significant challenge organizations face in tracking and protecting data that spans various platforms.
The complexity arises from the need to monitor and secure data across diverse environments, each with its own set of security protocols and vulnerabilities. Shadow data, which refers to unstructured or unmanaged data that exists outside of official cloud and SaaS systems, adds another layer of difficulty. Since shadow data is often unmonitored and unprotected, it can become a vulnerable point of entry for attackers.
Moreover, data involved in other workloads (such as cloud and even AI workloads) presents additional risks. Such systems often process vast amounts of data, which can sometimes be unencrypted or inadequately protected. This makes exposed data particularly susceptible to breaches if proper security measures are not in place. The dynamic nature of cloud workloads, coupled with the complexity of managing and securing data across different environments, amplifies the risk of both breaches and extended containment times.
How can you mitigate this? To address these challenges, organizations must adopt comprehensive security posture management strategies that include advanced monitoring tools and alert detection capabilities. Implementing solutions that offer visibility into cloud and SaaS environments is crucial for maintaining robust security and compliance. These solutions provide comprehensive insights into how cloud data and applications are distributed across various platforms, allowing organizations to detect and address misconfigurations that can expose vulnerabilities.
Preventing breaches with a comprehensive security tool
The most effective way to avoid the costs of a data breach is to prevent it from happening in the first place. Organizations can protect their cloud and SaaS infrastructure with an all-encompassing security posture management tool.
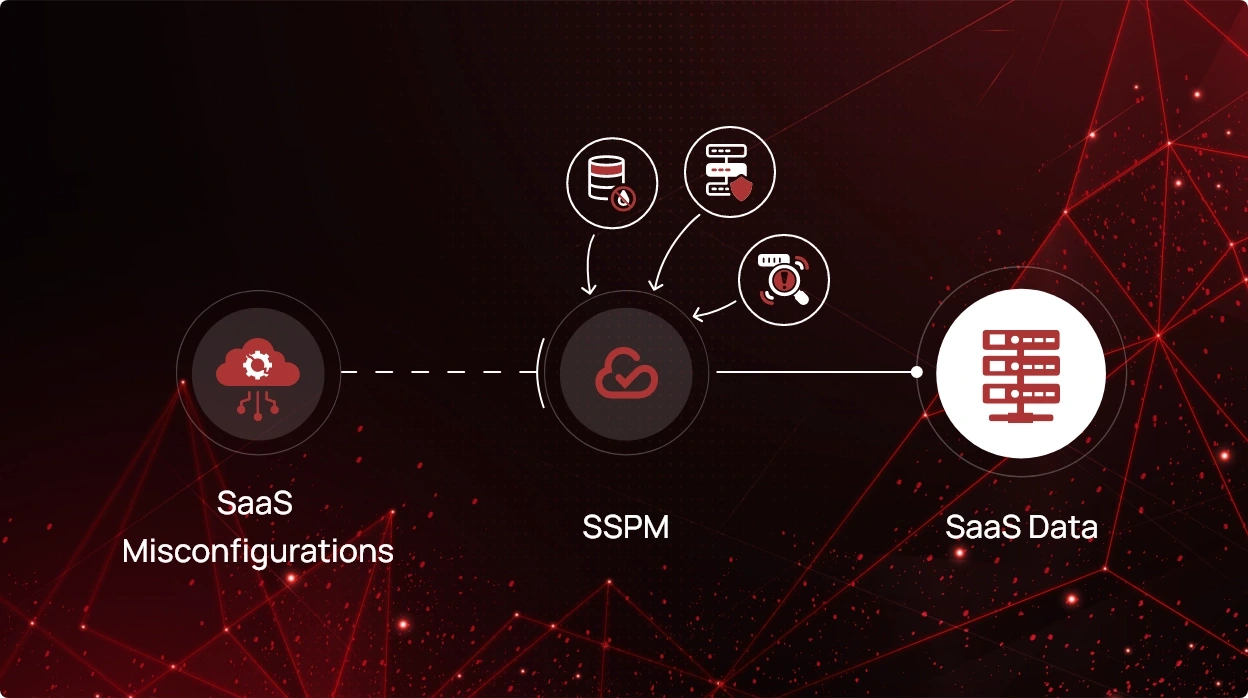
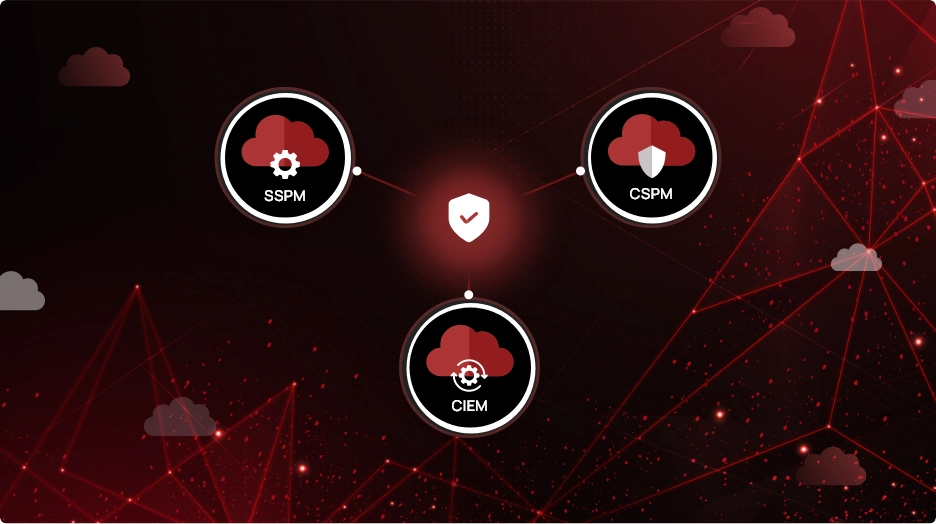
- SaaS Security Posture Management (SSPM) focuses on securing SaaS applications by monitoring and managing user access, data protection, and threat detection.
- Cloud Native Application Protection Platform (CNAPP) encompasses:
- Cloud Security Posture Management (CSPM) is essential for continuously assessing and managing cloud security configurations to prevent misconfigurations and compliance issues
- Cloud Infrastructure Entitlement Management (CIEM) is vital for managing user permissions and ensuring that access controls are correctly enforced.
- Cloud Workload Protection Platform (CWPP) is crucial for securing cloud environments by providing comprehensive visibility and control over workloads, ensuring vulnerabilities are managed and compliance is maintained.
- Continuous compliance monitoring helps ensure that security practices align with industry regulations and standards, reducing the risk of non-compliance penalties.
Together, these elements—visibility into cloud and SaaS environments, misconfiguration management, stringent identity and workload practices, and proactive compliance monitoring—create a comprehensive security framework that not only protects against threats but also fosters a resilient and compliant IT infrastructure.