Enhancing Cloud Security with MITRE ATT&CK: A Deep Dive into CheckRed’s Advanced Dashboard

In the rapidly evolving landscape of cybersecurity, understanding and mitigating threats requires a structured and comprehensive approach. MITRE ATT&CK® (Adversarial Tactics, Techniques, and Common Knowledge) provides a robust framework that helps organizations categorize and understand the tactics and techniques used by cyber adversaries throughout the various stages of an attack. Leveraging this framework, CheckRed offers an advanced dashboard that maps cloud matrix tactics and techniques to misconfiguration rules, providing extended visualization for all alerts concerning MITRE ATT&CK. This blog post will explore the MITRE ATT&CK framework, highlight the top tactics and techniques for misconfigurations, and provide a detailed walkthrough of our new dashboard.
What is MITRE ATT&CK?
MITRE ATT&CK is a globally recognized framework designed to provide a detailed categorization of adversary tactics, techniques, and procedures (TTPs). It breaks down the attack lifecycle into several stages, known as tactics, each representing a specific goal an attacker aims to achieve. Within each tactic, there are specific techniques that describe how attackers accomplish these goals. This structured approach helps organizations map security incidents to known attacker behavior, enhancing their threat detection, response, and overall cybersecurity posture.
Enhancing Cloud Security with MITRE ATT&CK
Understanding and mapping your security alerts to the MITRE ATT&CK framework provides several benefits:
- Improved Detection: By mapping alerts to MITRE ATT&CK framework, organizations can better detect and understand adversary behaviors.
- Enhanced Response: Understanding the tactics and techniques used by attackers allows for more effective incident response.
- Proactive Defense Strategies: By identifying potential attack patterns, organizations can implement proactive defense measures to mitigate risks before they manifest.
- Training and Awareness: The framework serves as a valuable training tool for security personnel, enhancing their understanding of adversary tactics and techniques.
- Gap Analysis: Helps in identifying gaps in existing security controls and processes, enabling targeted improvements and resource allocation.
Top Tactics and Techniques for Misconfigurations
Misconfigurations are a common and often critical vulnerability that attackers exploit. Here are some of the top tactics and techniques relevant to misconfigurations with some example rules:
Tactics
- Initial Access: Techniques used to gain an initial foothold within a network.
Example rules:- Ensure IAM users are managed centrally via identity federation or AWS Organizations for multi-account environments
- Ensure no Network ACLs allow ingress from 0.0.0.0/0 to remote server administration ports
- Lateral Movement: Techniques that allow attackers to move through a network.
Example rule:- Ensure the default security group of every VPC restricts all traffic
- Ensure routing tables for VPC peering are “least access”
- Privilege Escalation: Techniques that enable attackers to gain higher-level permissions.
Example rules:- Ensure security group changes are monitored.
- Ensure Network Access Control Lists (NACL) changes are monitored.
- Credential Access: Techniques used to steal credentials like usernames and passwords.
Example rules:- Ensure that EC2 Metadata Service only allows IMDSv2.
- Ensure Auto Minor Version Upgrade feature is Enabled for RDS Instances
- Defense Evasion: Techniques used to avoid detection and hide malicious activities.
Example rules:- Ensure VPC flow logging is enabled in all VPCs
- Ensure S3 bucket policy changes are monitored
Techniques
- Exploit Public-Facing Application: Taking advantage of vulnerabilities in applications that are exposed to the internet.
Example rules:- Ensure unauthorized API calls are monitored
- Ensure that HTTP(S) access from the Internet is evaluated and restricted
- Brute Force: Attackers exploit weak or misconfigured authentication mechanisms by repeatedly attempting various password combinations.
Example rules:- Ensure IAM password policy requires minimum length of 14 or greater
- Valid Accounts: Using valid credentials obtained from misconfigurations to gain access to systems.
Example rules:- Ensure access keys are rotated every 90 days or less
- Do not setup access keys during initial user setup for all IAM users that have a console password
- Account Manipulation: Exploiting misconfigured account settings to modify account attributes and escalate privileges.
Example rules:- Ensure IAM policy changes are monitored
- Ensure AWS Organizations changes are monitored
- Modify Cloud Compute Infrastructure: Misconfigurations in cloud settings that allow unauthorized changes to the cloud infrastructure.
Example rules:- Ensure AWS Security Hub is enabled
- Ensure that ‘Users can create security groups in Azure portals, API or PowerShell’ is set to ‘No’
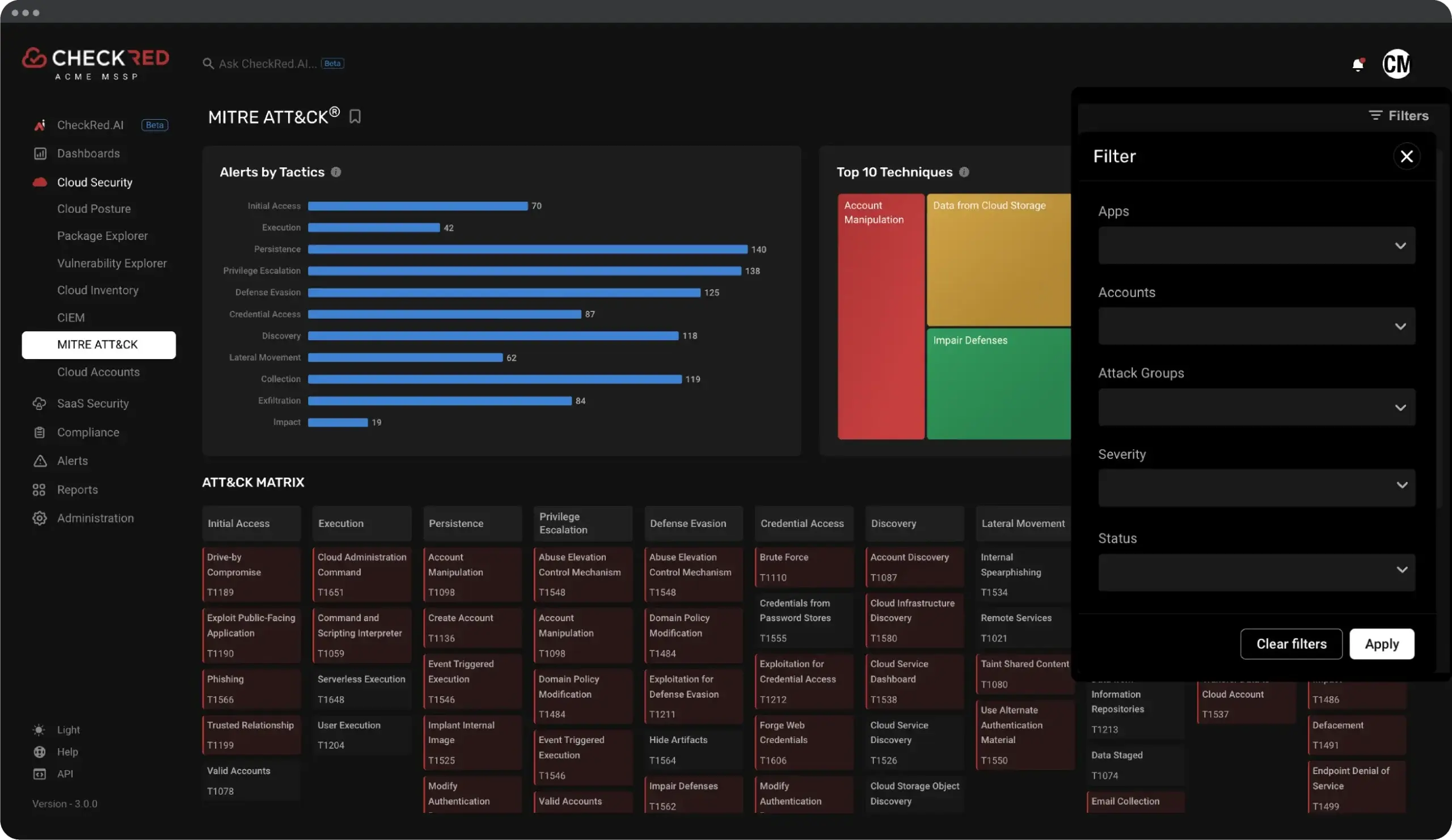
CheckRed MITRE ATT&CK Dashboard: Extending MITRE ATT&CK Visualization
At Checkred, we have developed an advanced dashboard that integrates MITRE ATT&CK with our misconfiguration detection rules. We have mapped misconfigurations to the MITRE ATT&CK framework tactics and techniques to help you get the attacker’s view.
This dashboard provides a visual representation of all alerts mapped to the relevant MITRE ATT&CK tactics and techniques. Here’s how our solution enhances security:
- Comprehensive Mapping: Misconfiguration rules in our system are mapped to MITRE ATT&CK tactic and technique, providing clear insights into potential attack vectors.
- Visual Representation: The dashboard offers an intuitive visualization of all detected misconfigurations and their corresponding MITRE ATT&CK mappings. This helps in quickly identifying the nature and potential impact of each alert.
- Prioritization of Alerts: By leveraging the MITRE ATT&CK framework, Checkred prioritizes alerts based on the severity and potential impact of the associated tactics and techniques.
- Detailed Insights: Each alert comes with detailed information, including the specific misconfiguration, the relevant MITRE ATT&CK technique, and recommended remediation steps.
- Continuous Monitoring: Our dashboard continuously monitors for misconfigurations, ensuring real-time detection and response to potential threats.
Detailed Walkthrough of the Dashboard
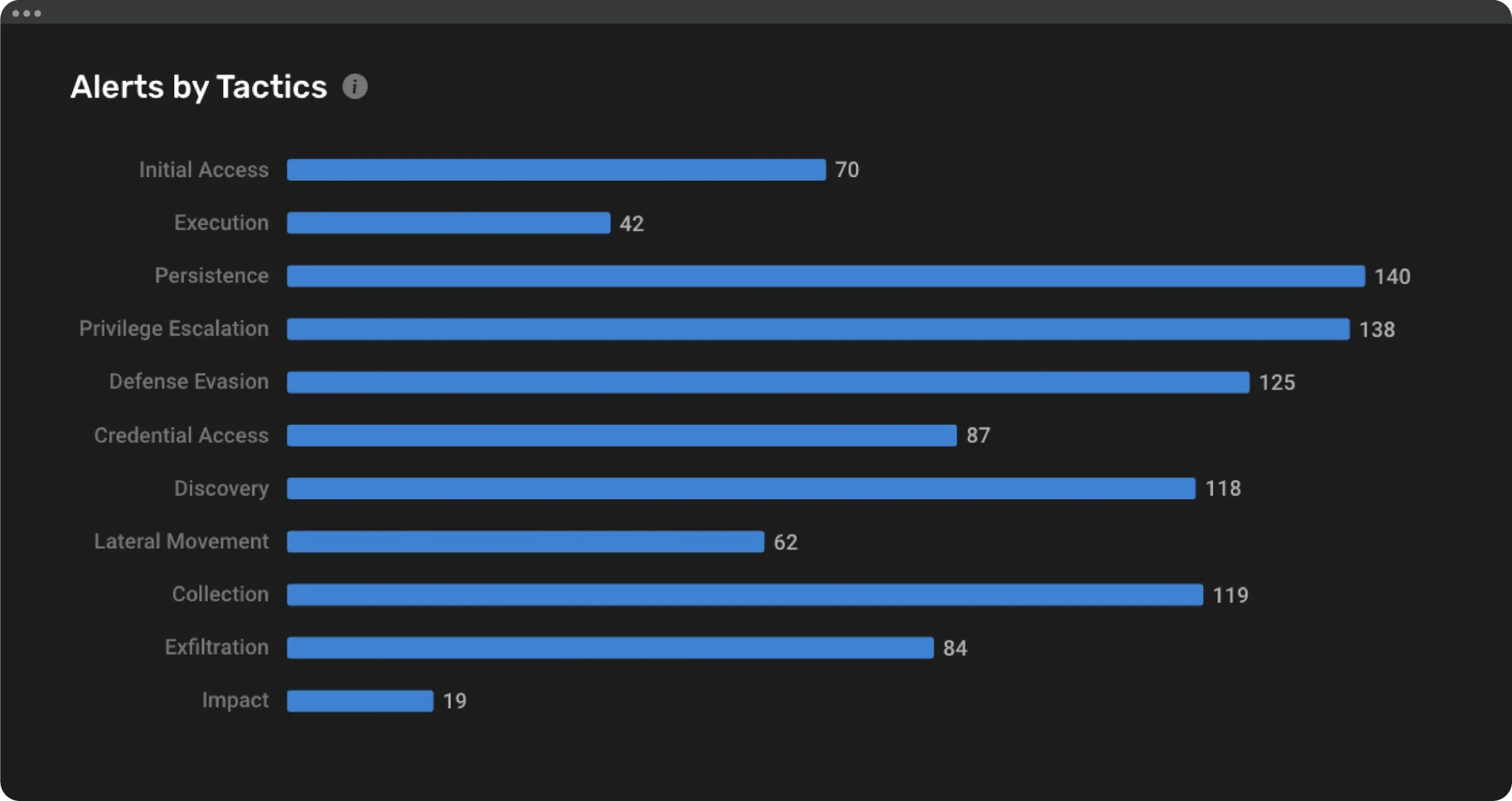
1. Alerts by Tactics
- Overview: The dashboard categorizes alerts by MITRE ATT&CK tactics, providing a high-level view of which phases of the attack lifecycle are most impacted.
- Benefits: Helps security teams quickly identify which stages of an attack are most vulnerable and prioritize response efforts accordingly.
- Visual Representation: Bar graphs showing the distribution of alerts across different tactics.
- Interactive Elements: Click on each tactic to drill down into selected tactic alerts and view detailed alert information.
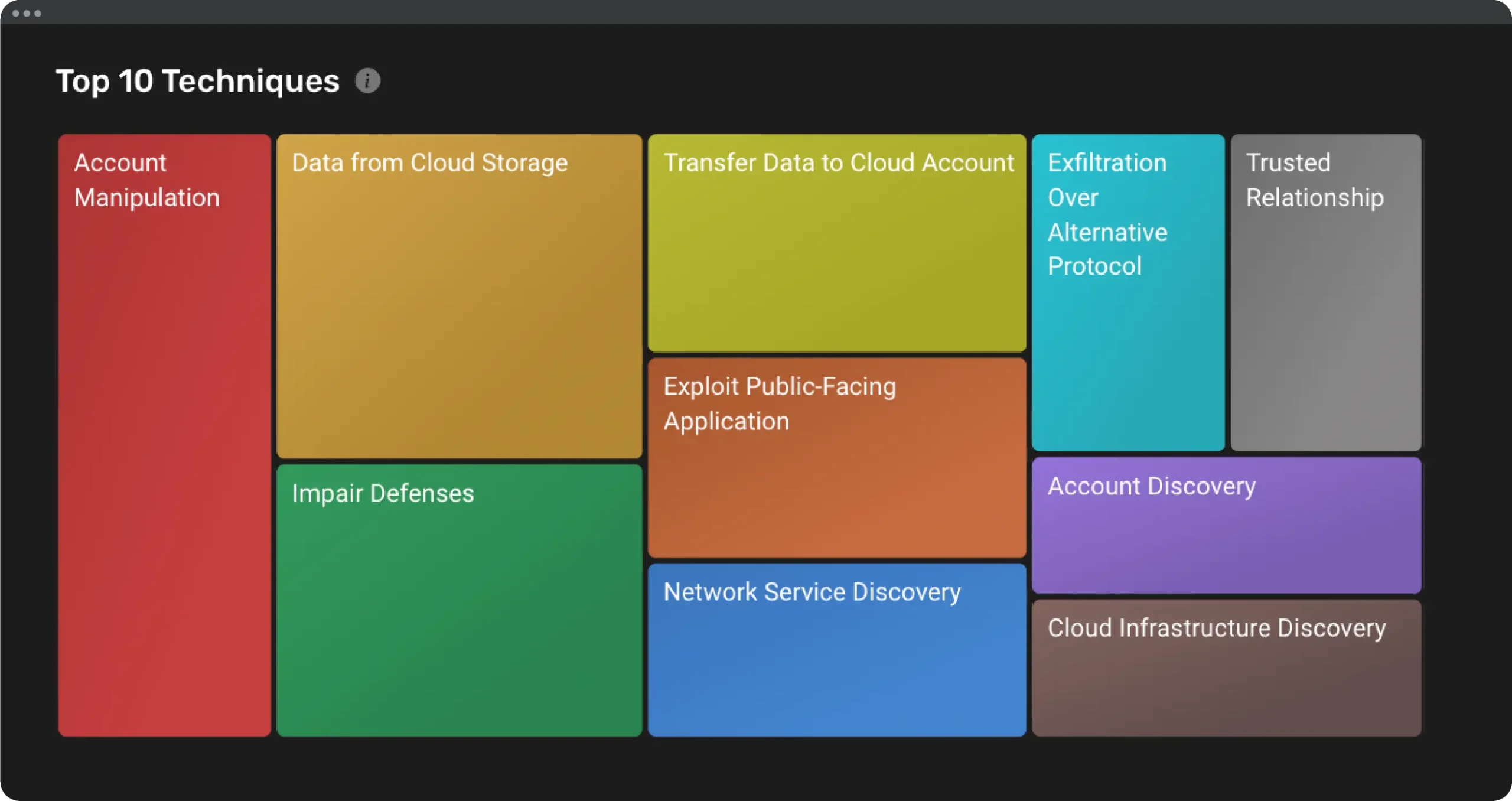
2. Top 10 Techniques
- Overview: Lists the top 10 most frequently triggered techniques based on number of detected misconfiguration alerts.
- Benefits: Highlights the most common attack methods, enabling teams to focus on mitigating these high-risk areas.
- Visual Representation: Graph showing the top 10 techniques, along with the number of alerts associated with each.
- Detailed Insights: For each technique, the dashboard provides information on the specific misconfigurations detected and recommended remediation steps.
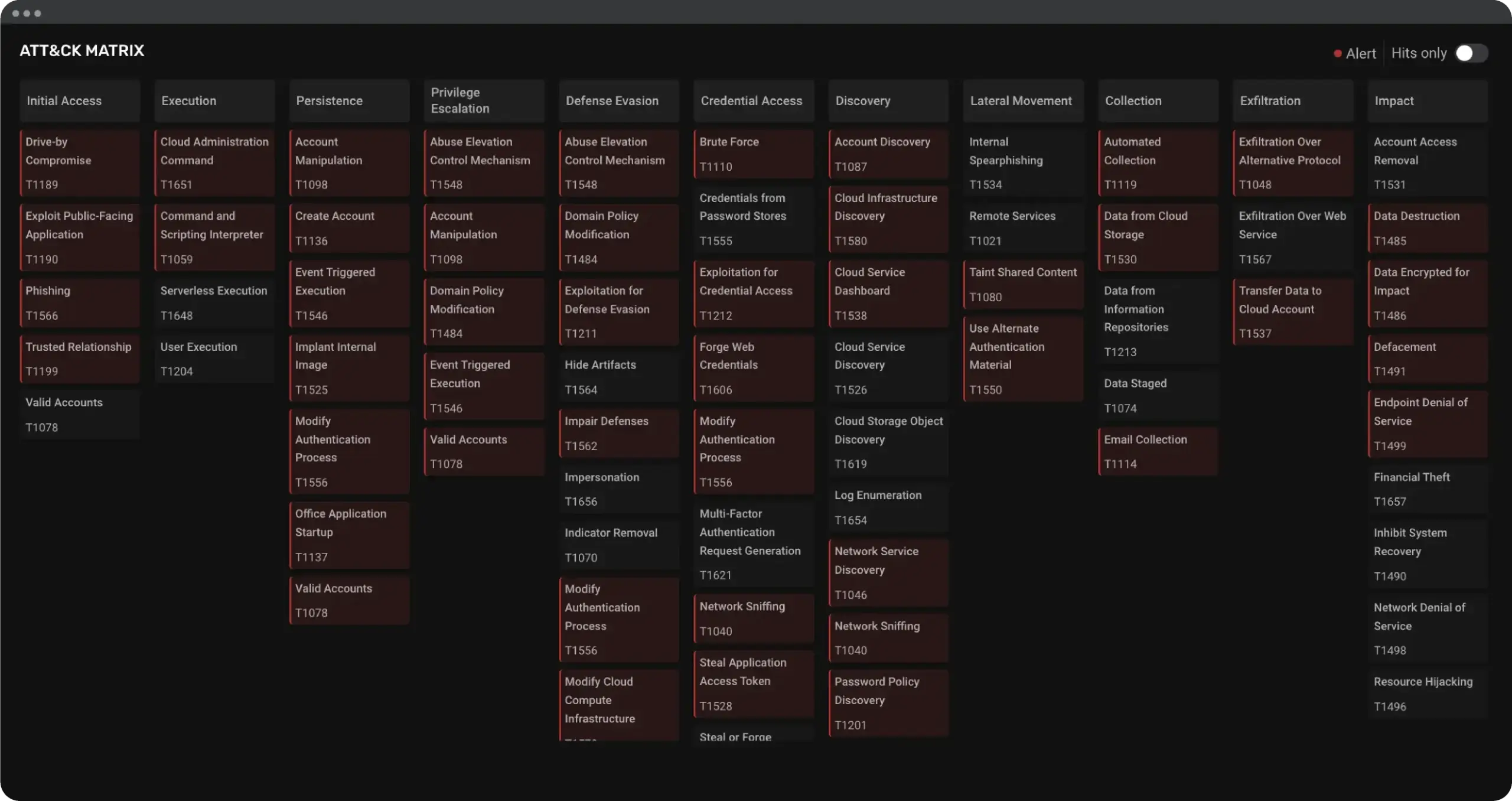
3. MITRE ATT&CK Matrix
- Overview: A visual representation of the MITRE ATT&CK matrix, showing all techniques with corresponding alerts or the absence thereof.
- Benefits: Provides a comprehensive view of the security landscape, making it easier to identify gaps in coverage and areas requiring immediate attention.
- Visual Representation: The MITRE ATT&CK matrix with color-code techniques based on the presence of alerts.
- Interactive Elements: Hover over or click on each technique to see detailed information about associated alerts due to misconfigurations.
- Alert Indicators: Techniques with active alerts are highlighted, while those without alerts are marked differently, providing a clear picture of the security posture.
4. MITRE ATT&CK Adversary Groups
- Overview: This feature allows users to filter and view techniques used by specific ATT&CK groups based on the MITRE database.
- Benefits: Helps organizations understand and defend against specific adversary groups by visualizing which techniques they commonly use.
- Visual Representation: Filtered view in the matrix wrt. ATT&CK groups and their associated techniques, showing the frequency and impact of each technique.
- Interactive Elements: Select different ATT&CK groups to see detailed information about the techniques they use and the related alerts in your environment.
Conclusion
In today’s digital era, ensuring cloud security is paramount as organizations increasingly depend on cloud environments. The MITRE ATT&CK framework plays a vital role by offering a structured method to understand and counteract adversary tactics and techniques.
CheckRed leverages MITRE ATT&CK to provide detailed insights into misconfigurations, enhancing threat detection and response. The dashboard’s features, including alerts by tactics, top techniques, and a comprehensive MITRE ATT&CK matrix, empower security teams to prioritize and address vulnerabilities efficiently and enables proactive defense measures, ensuring a robust security posture in the cloud.