Introduction to Active Directory Posture Management

Active Directory (AD) is a critical component of any organization’s IT infrastructure. Introduced by Microsoft over two decades ago, it has become the foundation for managing user identities, permissions, and access to resources within an enterprise network. It involves the systematic approach to safeguarding the security and integrity of Active Directory (AD) environments within organizations. It encompasses various practices aimed at maintaining a secure posture across AD infrastructure.
The primary objectives of Active Directory Risk Posture Management are:
- Ensuring integrity: Safeguarding the accuracy and reliability of AD data and operations against unauthorized changes or tampering.
- Maintaining availability: Ensuring AD services are continuously available to support organizational activities without disruption.
- Preserving confidentiality:Protecting sensitive information stored and processed within AD from unauthorized access and disclosure.
- Mitigating risks: Proactively identifying and addressing potential security vulnerabilities and misconfigurations that could be exploited by malicious actors.
Key components of Active Directory Risk Posture Management
Configuration management
Proper configuration settings are crucial to securing Active Directory (AD). Misconfigurations can create significant security vulnerabilities, making it easier for attackers to exploit your system. For instance, enabling unconstrained Kerberos delegation can allow attackers to impersonate users and access sensitive resources. Similarly, improper settings in the AdminSDHolder can leave privileged accounts exposed to attacks. Ensuring correct and secure configurations helps protect against unauthorized access and potential breaches.
Privilege management
The principle of least privilege (PoLP) is fundamental in managing AD security. This principle means granting users only the permissions they need to perform their jobs and nothing more. By minimizing the number of users with high-level access, you reduce the risk of privilege escalation attacks. Regularly reviewing and adjusting user privileges and group memberships is essential to maintaining a secure environment. Over-permissioned accounts can provide easy entry points for attackers, so it is essential to keep privileges in check.
Policy enforcement
Consistent enforcement of security policies is another key aspect of AD risk posture management. Policies like strong password requirements and account lockout settings are essential for protecting against unauthorized access. Strong password policies should enforce complexity, length, and regular updates to prevent brute force and password spray attacks. Account lockout policies can prevent repeated login attempts from automated attacks.
Additionally, policies governing the use of service accounts, such as ensuring they have limited privileges and regularly updating their passwords, are critical. Enforcing these policies consistently across the organization helps maintain a robust security posture.
Challenges in Active Directory Posture Management
Managing Active Directory (AD) effectively is not without its challenges, especially in today’s complex IT landscape.
Complexity of AD environments
Active Directory serves as the backbone of user authentication, access management, and policy enforcement for organizations of all sizes. However, as organizations grow, so does the complexity of their AD environments. Large enterprises often have sprawling AD infrastructures spread across multiple geographic locations, encompassing numerous domains, forests, and trusts.
In addition to size, the rise of hybrid and multi-cloud environments further complicates AD management. Integrating on-premises AD with cloud services such as Azure AD or AWS Directory Service requires careful planning and execution. Ensuring seamless authentication and access control across these environments while maintaining security posture adds layers of complexity.
Lack of coordination between IT and security teams
A significant hurdle in maintaining a robust AD security posture is the frequent disconnect between IT operations and security teams. IT teams are primarily focused on ensuring the availability and functionality of AD services to support day-to-day business operations. They manage user accounts, group memberships, and handle routine maintenance tasks to keep AD running smoothly.
On the other hand, security teams are responsible for safeguarding AD against threats, enforcing security policies, and detecting suspicious activities. They prioritize risk mitigation, compliance adherence, and threat prevention.
This separation in priorities and responsibilities can lead to gaps in AD security. IT teams may inadvertently implement configurations that compromise security for the sake of operational efficiency. Meanwhile, security teams may struggle to enforce stringent security policies effectively due to lack of visibility into operational workflows or inadequate communication with IT counterparts.
The role of automation and tools in AD Posture Management
Automating routine tasks:
Automation plays a crucial role in maintaining a secure posture for Active Directory (AD) by streamlining repetitive tasks and reducing human error. Specifically, automation can handle tasks like privilege reviews and policy enforcement with efficiency and accuracy.
Privilege reviews, for example, are essential to ensure that users have the appropriate level of access based on their roles within the organization. Automating this process allows for regular audits without overwhelming IT teams with manual reviews. For example, policy enforcement, for password complexity and expiration in AD, can be automated. This not only strengthens security but also ensures compliance with internal policies and regulatory requirements.
Utilizing advanced tools:
Specialized tools designed for AD posture management enhance security and compliance by providing advanced capabilities beyond what native AD tools offer. These tools typically include features like real-time monitoring, anomaly detection, and automated remediation.
By leveraging these tools, organizations gain a deeper insight into AD environments, identifying potential vulnerabilities and misconfigurations proactively. They enable continuous monitoring of AD activities, detecting suspicious behavior or unauthorized changes promptly. Additionally, advanced tools facilitate rapid response to security incidents, minimizing the impact of breaches or threats.
Leveraging CheckRed for robust AD Posture Management
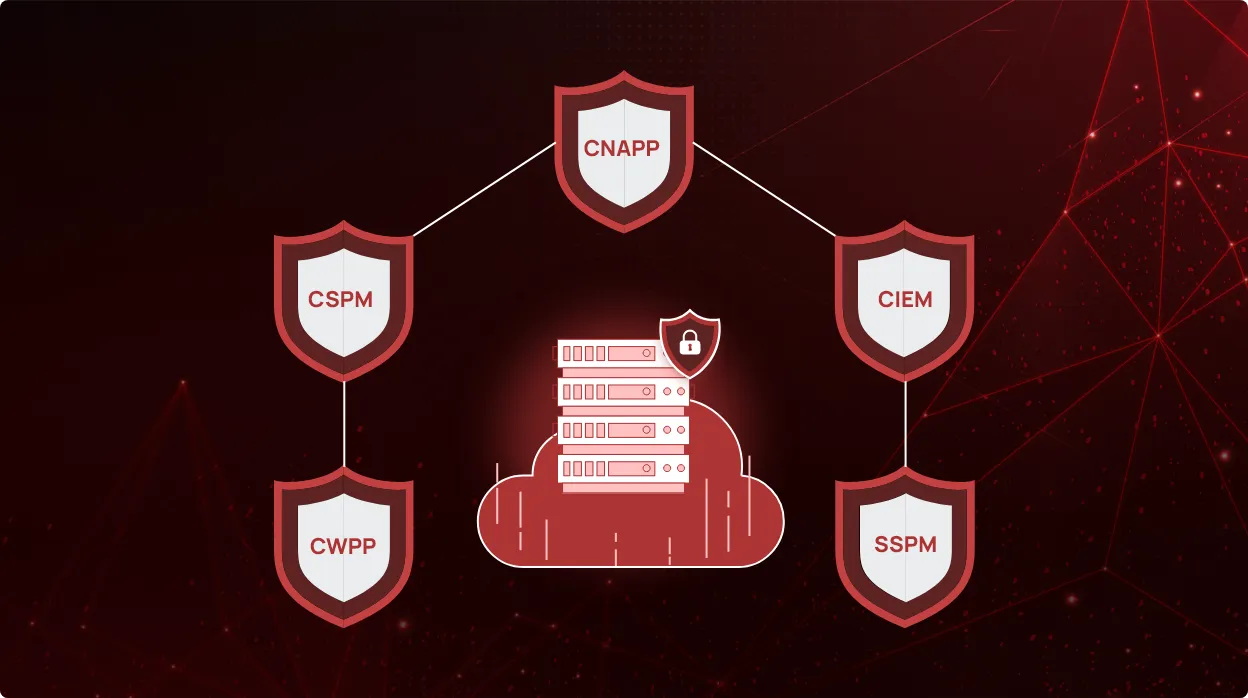
CheckRed’s Complete Cloud Security Solution (CNAPP) integrates Cloud Security Posture Management (CSPM), Cloud Infrastructure Entitlement Management (CIEM), and Cloud Workload Protection Platform (CWPP), along with SaaS Security Posture Management (SSPM) into a unified platform. This holistic approach provides organizations with comprehensive visibility and control over their cloud environments, including AD.
Implementing and maintaining a robust AD risk posture is simplified with CheckRed. The platform offers centralized management and automation of AD security configurations, policies, and privileges. By leveraging CheckRed’s integrated solution, organizations can effectively prevent misconfigurations, enforce stringent security policies, and manage user privileges with ease.
CheckRed empowers IT and security teams to align their efforts seamlessly, bridging the gap between operations and security. Organizations can proactively secure their AD infrastructure against emerging threats and compliance risks, ensuring continuous protection and operational efficiency.