The overwhelming number of security alerts that need to be addressed in a user's cloud environment can often cause mental...
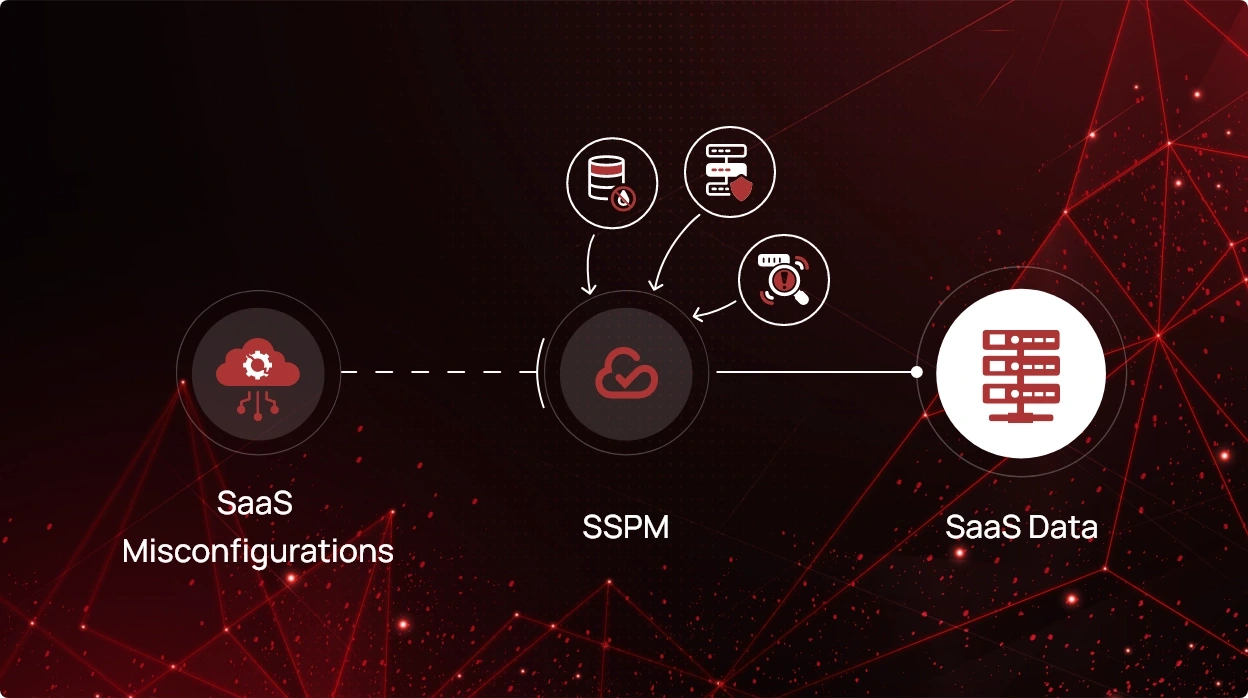
The ramifications of SaaS misconfigurations
In the current business landscape, SaaS applications have become an essential part of day-to-day operations. From file...
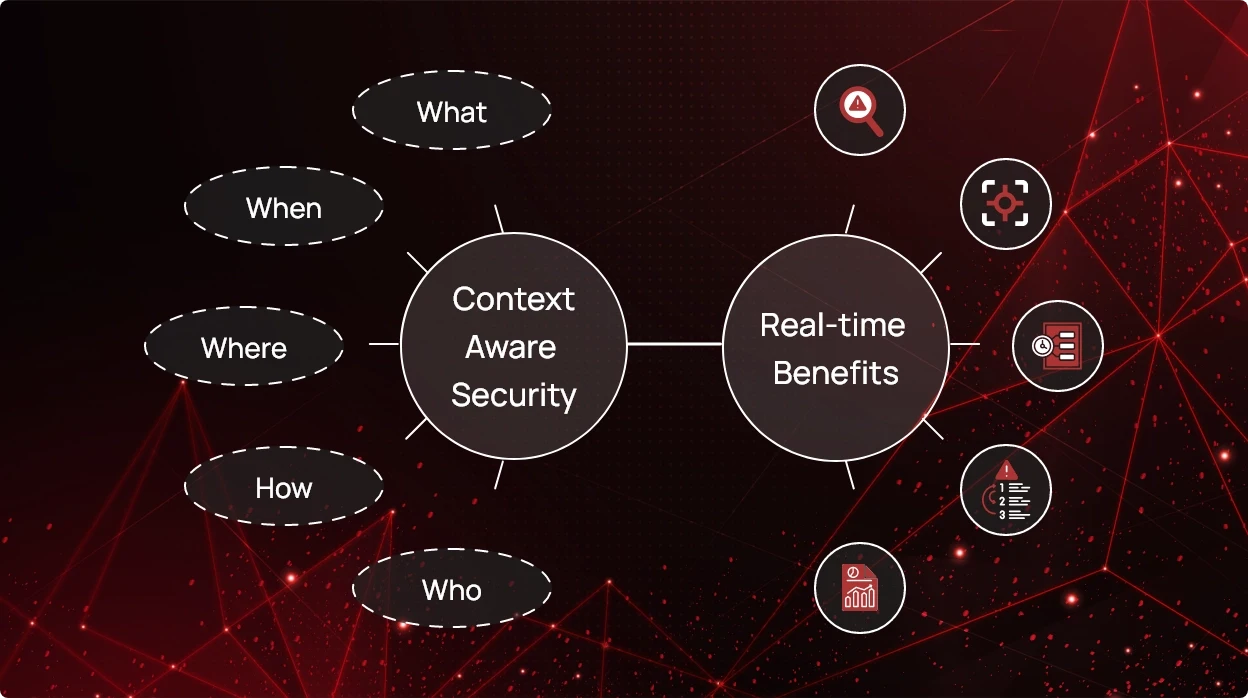
Context-aware Security and its Real-time Benefits
Traditional defenses like firewalls and antivirus technologies struggle to keep up with the rate of emerging threats in the...
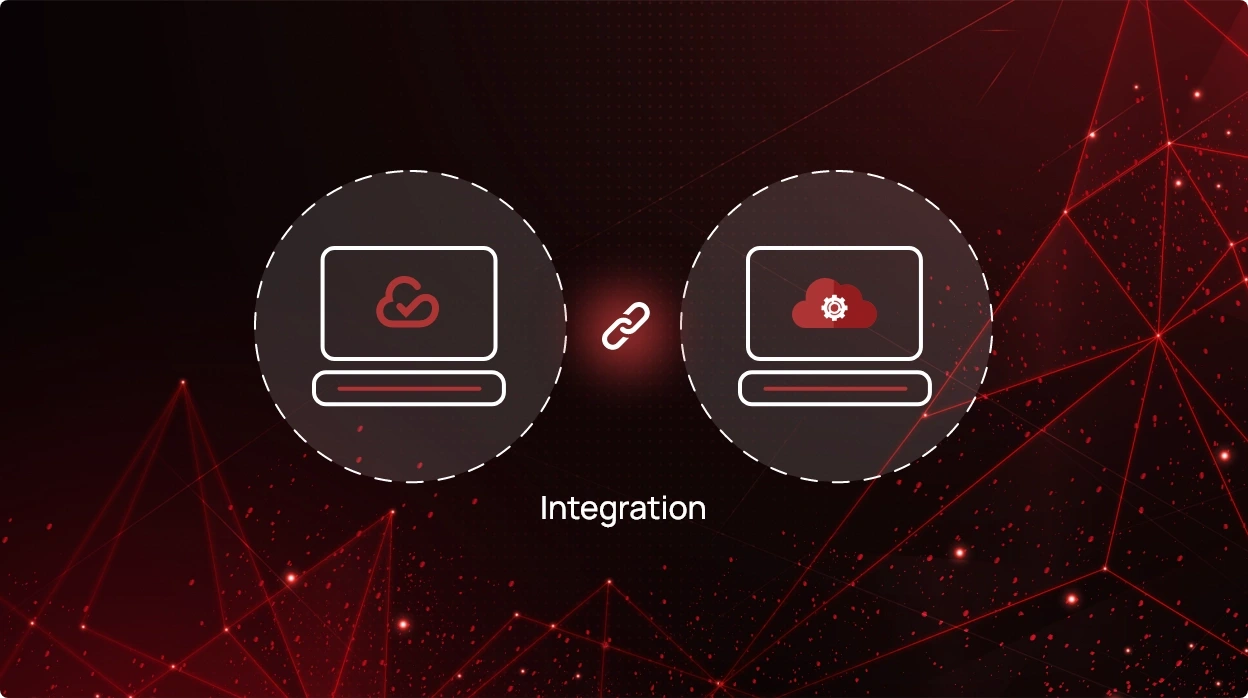
How Can Technology Integrations Improve Security Posture?
Applications that integrate with each other, removing data silos and connecting business operations, create a smart and...
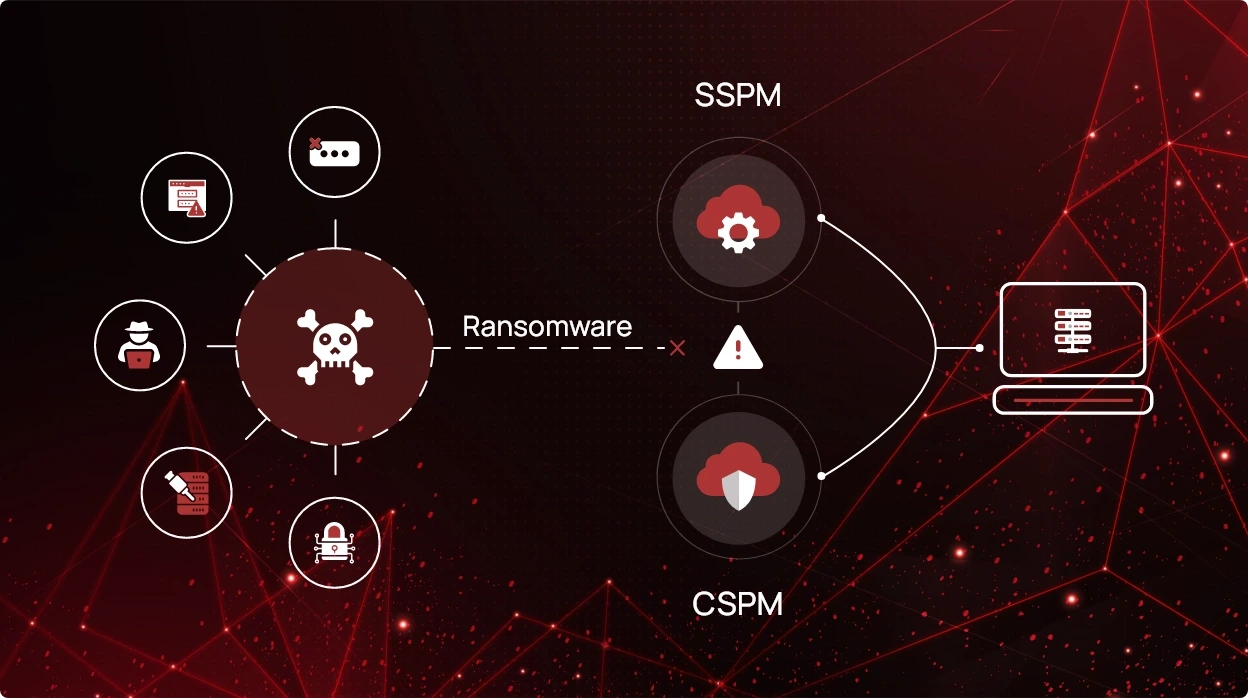
Prevent Ransomware with SaaS and Cloud Security
Ransomware poses a major threat to organizations worldwide. Hackers employ it to infect business systems, steal sensitive...
Public vs. Private Cloud Security
When it comes to cloud computing, two fundamental and distinct models take center stage: public and private clouds. As data...
Navigating Data Protection and SaaS Security
In the dynamic landscape of Software as a Service (SaaS) applications, the inadvertent exposure of sensitive data due to...
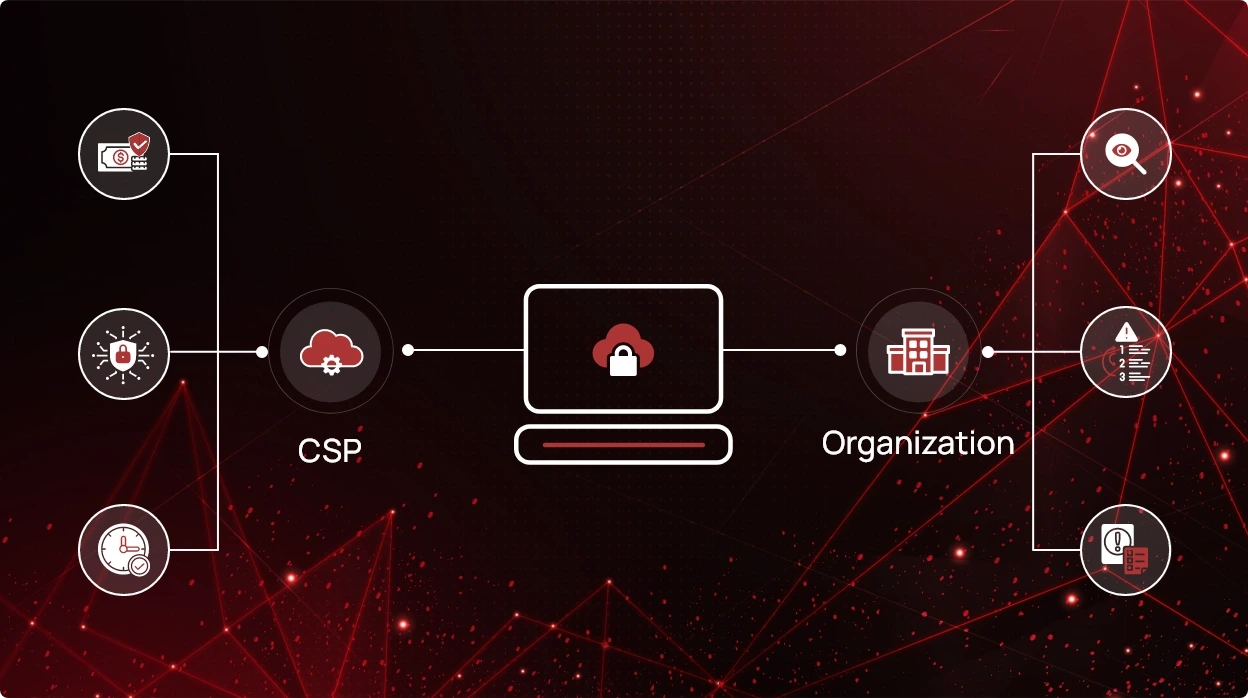
Shared Responsibility Model and Cloud Security
Embracing cloud infrastructure demands a mindset shift, moving beyond traditional elements like firewalls to focus on...
Enhancing visibility across multi-cloud environments
In today's fast-paced digital landscape, businesses are increasingly adopting multi-cloud environments to leverage the...