On December 16, 2024, a hacker named "IntelBroker" leaked 2.9 gigabytes of data from Cisco's DevHub platform onto...
The U.S. Treasury Hack: A Wake-up Call for Implementing Strong Identity Access Management
The recent cyberattack on the U.S. Treasury, confirmed on December 30, 2024, has brought to light the critical need for...
2024 in SaaS Breaches – A Recap
Throughout 2024, the Software as a Service (SaaS) landscape saw significant growth, with businesses increasingly relying on...
Securing Healthcare in the Cloud: Key Insights from the Liverpool Cyberattack
As SaaS apps and cloud services become central to healthcare operations, security vulnerabilities also increase. An...
Defending Against Advanced Identity-Based Attacks
Identity-based attacks have become more sophisticated and prevalent as organizations adopt stronger authentication methods...
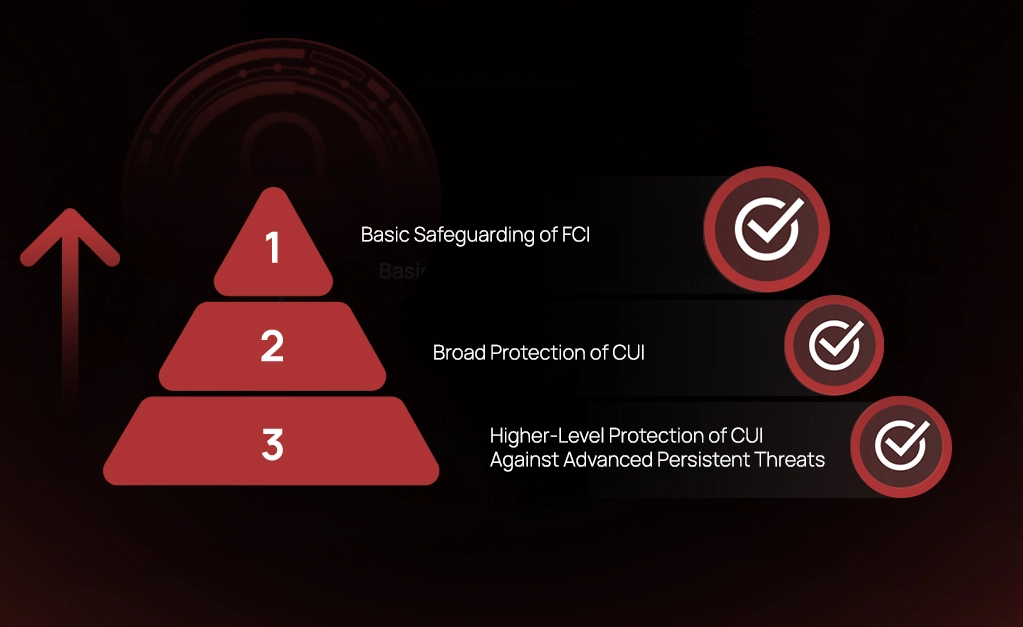
Understanding CMMC 2.0 – A Guide for MSPs and MSSPs
As an MSP or MSSP, helping your clients navigate the complexities of cybersecurity is a critical part of your...
EmeraldWhale – Major Cyberattack Involving 15,000 Cloud Credentials and Exposed GitHub Configurations
A major cyberattack occurred just a few weeks ago, and is quite the serious wake-up call for organizations using cloud...
Misleading Disclosures About Cyberattacks Can Cost You Millions!
The Securities and Exchange Commission has charged four prominent companies—Unisys Corp., Avaya Holdings, Check Point...
Google Cloud Update – Mandatory Multi-factor Authentication (MFA) by 2025
In a move to bolster security and protect against rising cyber threats, Google is making Multi-factor Authentication (MFA)...