Silos are adversely affecting your security culture
In cloud computing, security is an ongoing concern of a critical nature. It’s not just about having robust tools and technologies in place; it’s about cultivating a culture where security is ingrained into every aspect of operations.
In an organization’s online business structure, there are multiple elements or components that make up its security framework. They work diligently, but what if there is a lapse in communication? What if one component spots a risk but the information fails to reach other components? This lack of coordination creates silos in security operations.
Silos refer to the division and isolation of teams, tools, or departments within an organization. Instead of working together seamlessly, these entities operate independently, often without sharing crucial information or insights.
Silos can develop between different departments, such as IT operations and security. While IT operations teams focus on maintaining the functionality and performance of systems, security teams prioritize protecting these systems from threats. Without effective collaboration and communication between these departments, security vulnerabilities may go unnoticed until it’s too late.
Challenges of platform fatigue
Platform fatigue is one of the most prevalent and serious concerns in modern business operations, and it can wear down teams and deteriorate productivity. In cybersecurity, platform fatigue refers to the exhaustion and frustration that arise from managing a multitude of disparate security tools.
The increase in the number of disparate security tools creates an ongoing struggle within an organization that, by choice or need, employs more than a manageable number of them. Each tool may serve a specific purpose, whether it’s monitoring network traffic, scanning for vulnerabilities, or detecting malicious activity. However, as the number of tools increases, so does the complexity of managing them all. Integrating these tools, ensuring they’re properly configured, and interpreting the flood of alerts they generate can quickly become overwhelming.
Managing multiple security tools that operate in isolation can lead to the following consequences:
- Inefficiency is first observed when security teams spend more time managing tools than actually addressing security risks. Instead of focusing on proactive measures to enhance security, they find themselves caught up in administrative tasks such as updating software, correlating alerts from different tools, and manually remediating issues.
- Second, increased complexity arises from the tangled web of integrations, configurations, and dependencies that come with managing multiple security tools. As complexity increases, so does the likelihood of misconfigurations, oversight, and errors, which can inadvertently create security vulnerabilities.
- Decreased effectiveness is perhaps the most concerning consequence of platform fatigue. When security teams are overwhelmed by the sheer volume of tools and alerts, they may become desensitized to genuine threats or overlook critical vulnerabilities. This tunnel vision not only diminishes the organization’s ability to detect and respond to security incidents promptly but also exposes it to heightened risk.
Consolidating security tools: A solution to security silos
Consolidating security tools brings order to chaos. By centralizing security functions into a single platform, organizations can promote collaboration, streamline workflows, and enhance visibility across their security operations.
When everyone uses the same tools and speaks the same language, collaboration is fostered. Security teams can streamline their efforts to successfully manage security threats, share information, and communicate when they have access to a single platform. They collaborate as a unified team to protect the company’s digital assets rather than remaining isolated in their separate silos.
Consolidating security tools also offers the obvious advantage of streamlining workflows. Security teams frequently find themselves switching between several interfaces, manually correlating data, and duplicating effort when using different tools. On the other hand, workflows become more streamlined and efficient when using a single integrated platform. Without having to navigate between many programs, security analysts can access all the tools and information they need from a single dashboard, which lowers the possibility of mistakes or oversights.
Consolidating security tools also offers the organization’s security posture more visibility. Organizations get an extensive view of their security landscape from a single pane of glass as opposed to trying to piece together fragmented insights from multiple tools. This increased visibility empowers security teams to recognize patterns, spot irregularities, and take proactive measures to counter risks, which improves the organization’s overall security posture.
CheckRed: A comprehensive solution
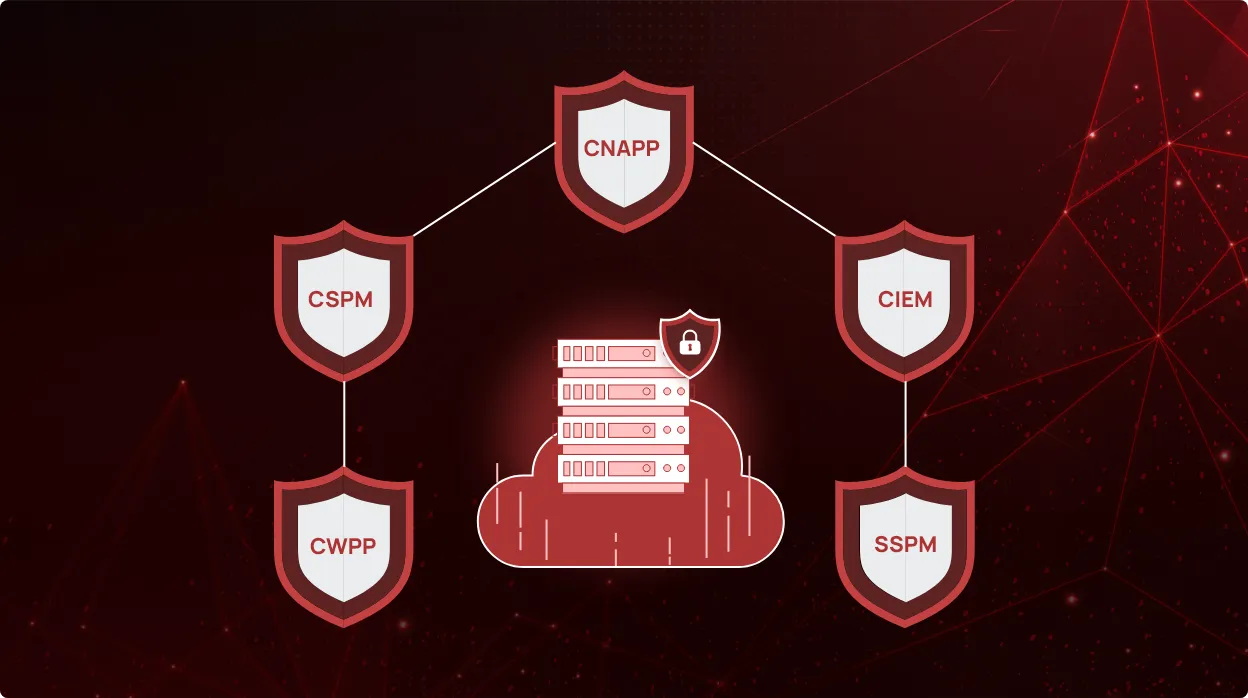
CheckRed is a one-stop solution for all things SaaS and cloud security. The multi-tenant platform comprises 5 essential components.
- CNAPP (Cloud-Native Application Protection Platform) ensures the security of cloud native applications and addresses the diverse security challenges posed by cloud-native architectures, including containerized environments, serverless computing, and microservices.
- CSPM (Cloud Security Posture Management) continuously monitors your cloud environment, identifying misconfigurations, compliance violations, and security risks.
- CIEM (Cloud Infrastructure Entitlement Management) protects identities and permissions across all cloud services (SaaS, IaaS, PaaS) to stop unauthorized access and overly permissive roles from causing a data breach.
- CWPP (Cloud Workload Protection Platform) provides real-time detection of workload risks and comprehensive protection of your entire cloud, empowering security teams with the right tools to fit their requirements.
- SSPM (SaaS Security Posture Management) extends a protective umbrella to your SaaS applications. It scrutinizes SaaS environments, identifying vulnerabilities, data exposure risks, and compliance gaps to ensure the integrity and confidentiality of your sensitive data.
By consolidating CNAPP, CSPM, CIEM, CWPP, and SSPM into a single, unified platform, CheckRed eliminates the fragmentation and complexity associated with managing disparate security tools. By providing a comprehensive suite of cloud security solutions, CheckRed empowers organizations to cultivate a strong security culture. This integrated approach not only promotes collaboration and communication across security teams but also streamlines workflows and enhances visibility into the organization’s security posture.