Navigating Data Protection and SaaS Security
In the dynamic landscape of Software as a Service (SaaS) applications, the inadvertent exposure of sensitive data due to misconfigurations is a constant, pressing concern. Instances of such data leakages can result in financial consequences, erode user confidence, and tarnish a company’s reputation. SaaS security management plays a pivotal role in mitigating these challenges. It’s imperative to understand how minimizing these misconfigurations is an anchor for sustaining data security within SaaS environments.
Understanding Data Leakages Due to Misconfigurations
Data leakages stemming from misconfigurations in SaaS applications occur when sensitive information is inadvertently exposed to unauthorized parties. In the realm of SaaS, this arises from the accidental transfer of data from an organization to external sources. It encompasses confidential customer data, financial records, strategic documents, and more – all of which should remain internal.
Prominent cloud platforms like Google Workspace, Microsoft 365, Salesforce, and Slack are susceptible to such leaks due to intricate SaaS security processes. In a dynamic digital environment, where a single click can compromise data, enterprises face substantial risks. Combatting data leaks is paramount due to potential reputation damage, hefty fines, and legal repercussions. Key leak categories include:
- Shared Data by End-Users: SaaS ease of data sharing can lead to costly unintended exposure
- Risky SaaS Applications: Insecurely developed or malicious apps from cloud marketplaces can compromise data
- Cloud Ransomware: Hackers may release data to extort organizations, necessitating proactive defense
Sensitive data categories at risk include identity details, activity histories, and credit card information. Attackers exploit weak encryption, software vulnerabilities, and inadequately monitored cloud environments.
Prevention involves vigilant communication channel monitoring and integrating security measures into SaaS procedures. As SaaS models evolve, companies must prioritize security, address misconfigurations, and uphold tenant compliance. Cloud Service Providers play a pivotal role in enforcing stringent security measures.
Where Can SaaS Misconfigurations Arise From?
- Inadequate Access Controls: Incorrect permissions can result in data breaches
- Weak Authentication: Poor user authentication facilitates unauthorized access
- Exposed APIs: Unsecured APIs expose critical data
- Publicly Accessible Storage: Misconfigured cloud storage also exposes private data
- Unpatched Software: Neglected updates lead to vulnerabilities
To counter these risks, organizations must proactively enforce access controls, robust authentication, and regular audits. Swiftly addressing misconfigurations enhances data security.
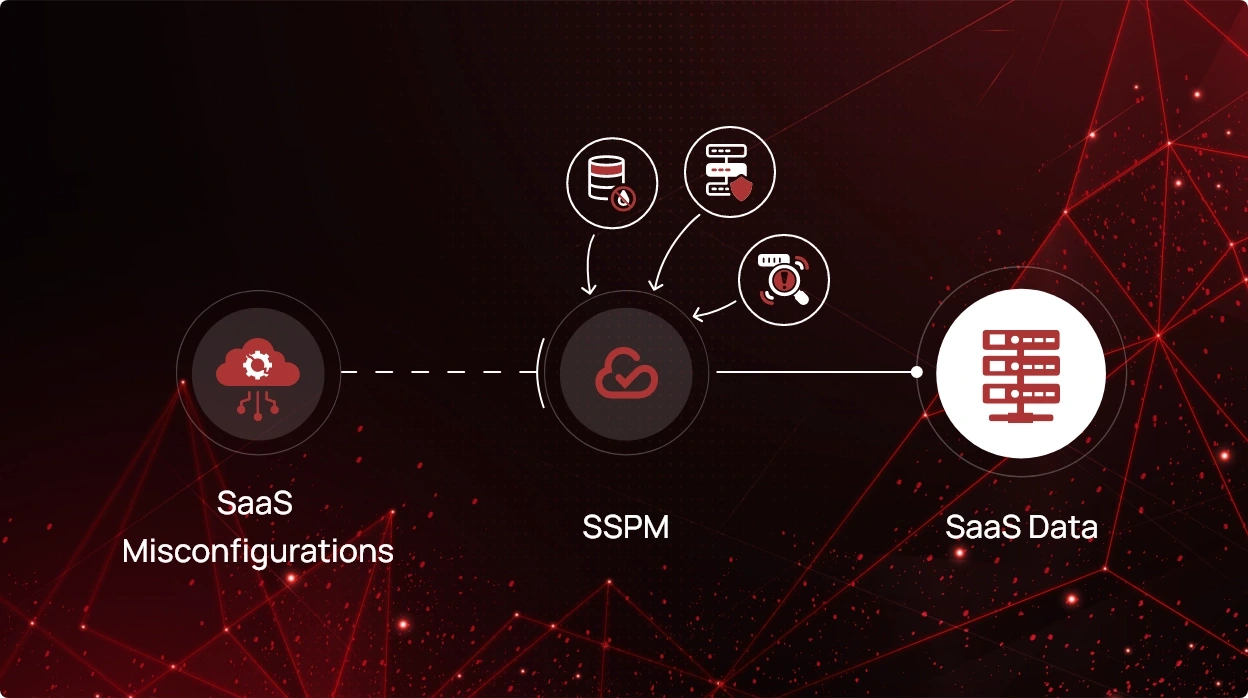
The Role of SSPM Tools in SaaS Security
SaaS Security Posture Management (SSPM) tools like CheckRed play a pivotal role in bolstering SaaS security. These tools are designed to identify, assess, and guide in the rectification of misconfigurations that can lead to data leakages. Their significance lies in their ability to help in the proactive enhancement of SaaS security management measures.
Identifying and Mitigating Misconfigurations:
- SSPM tools automatically scan configurations and access controls, pinpointing potential risks
- They offer guidance on remediating misconfigurations promptly, reducing the risk of data exposure
Enhancing Overall SaaS Security:
- SSPM tools provide continuous monitoring, ensuring that security remains robust over time
- By integrating with the software development process, they instill security measures from the earliest stages
SSPM platforms aid in complying with industry standards and fostering a culture of advanced data protection. Considering the complexities associated with SaaS applications, SSPM tools serve as vigilant guardians, fortifying defenses against data leakages arising from misconfigurations.
SSPM is an example of how security professionals are moving away from simple detection and response and towards a proactive strategy. Businesses using multiple SaaS apps face security issues as SaaS spending soars every year. In this situation, SSPM is a trustworthy method for automating the detection and guided correction of SaaS misconfigurations.
Key Features of SSPM Tools:
- Automated Assessment: Swift scans by SSPM tools identify potential security gaps
- Policy Enforcement: SSPM tools ensure configurations align with security policies and best practices
- Remediation Guidance: Actionable guidance aids prompt and effective misconfiguration correction
- Continuous Monitoring: Ongoing surveillance maintains a resilient security posture over time
- Integration with SDLC: SSPM tools seamlessly embed security into the software development lifecycle
- Compliance Management: The tools assist in adhering to industry standards, promoting advanced data protection
Benefits of SSPM Tools in SaaS Security:
- Enhanced Data Protection: SSPM tools prevent unauthorized access to sensitive data, thereby strengthening SaaS data protection
- Early Detection and Mitigation: Identifying misconfigurations early averts potential data leakages
Incorporating SSPM tools such as CheckRed, empowers organizations with a proactive defense mechanism against data leakage risks resulting from misconfigurations. In an evolving landscape, these tools stand as sentinels, guarding SaaS environments and upholding the integrity of data security.