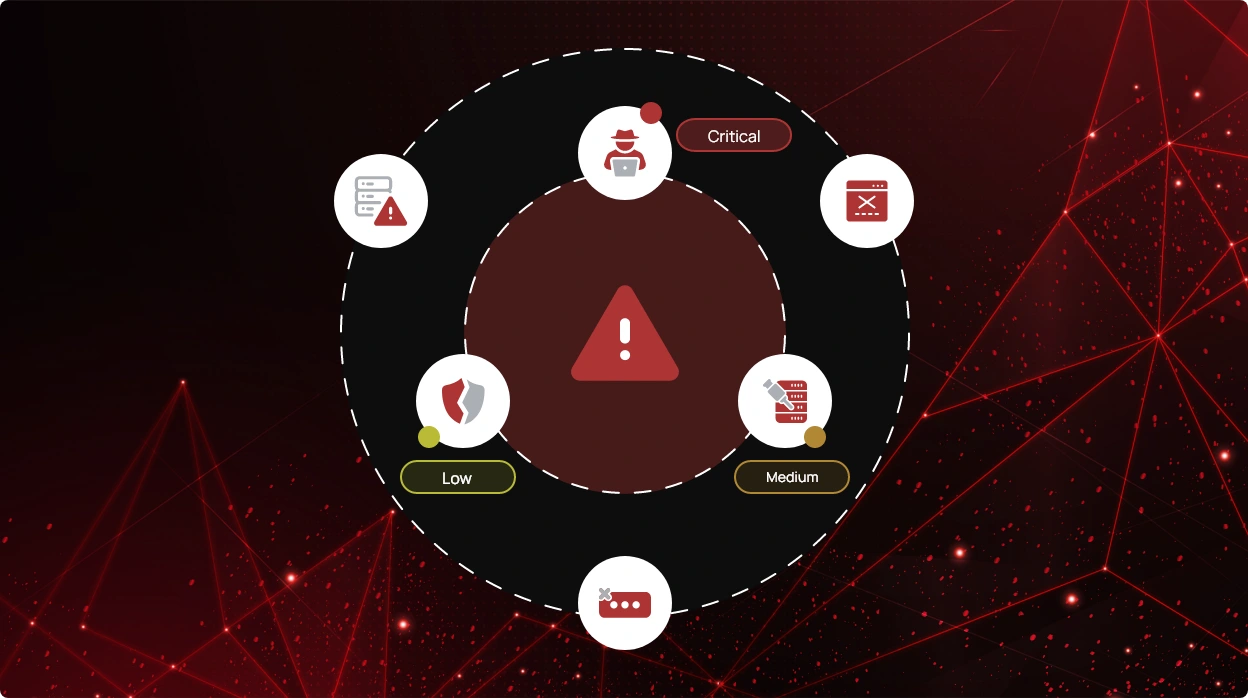
Alert Prioritization
SaaS and cloud environments are essential for establishing a competitive edge in the ever-evolving digital world we navigate every day. However, there are serious security challenges that come along with the rising reliance on cloud computing.
Your organization’s total strength and adaptability of its security controls in various settings are reflected in your security posture. Effective alert prioritization is one of the most important aspects of maintaining a strong security posture. Organizations can promptly handle urgent threats, lower risks, and safeguard critical assets by prioritizing the appropriate notifications.
Continue reading as we discuss why alert prioritization is crucial for protecting the security of your SaaS and cloud infrastructure.
Understanding the need for risk categorization
For effective security posture management, SaaS and cloud security tools must effectively categorize and prioritize alerts. Organizations can better comprehend the possible impact on their overall security by categorizing warnings into distinct risk levels as critical, high, medium, and low.
Not all alerts represent the same level of risk, so this distinction is crucial. Particularly urgent attention is required for critical warnings because they indicate serious security risks with potentially significant repercussions. Unauthorized access, data leaks, or misconfigurations could be the subject of these high-priority alerts. Ignoring them could endanger an organization’s reputation, data integrity, and financial stability.
By prioritizing critical alerts, organizations can allocate resources effectively and promptly address the most urgent security risks, minimizing potential damage and safeguarding their valuable assets.
Establishing proper criteria for alerts
Effective alert prioritization in SaaS and cloud contexts requires the establishment of suitable classification criteria. Organizations can accurately assess the gravity and possible impact of each warning by establishing explicit rules and frameworks. When creating these criteria, it is important to take risk intensity, exploitability, and potential consequences into account.
A focused approach is ensured by tailoring the criteria to the organization’s particular security requirements. Working together with security teams, IT, and other stakeholders enables the definition of relevant criteria that are compatible with the context and goals of the organization. Organizations may concentrate on high-risk warnings thanks to customized criteria, which facilitates effective resource allocation and proactive patching of security flaws.
The importance of context
In SaaS and cloud systems, context is essential for prioritizing warnings efficiently. Knowing the alert context is essential to understanding the nature and potential consequences of a security concern. User behavior and damaged assets are a couple of the factors that affect the entire context.
Security teams can concentrate their attention on signals that represent urgent hazards and demand immediate action thanks to contextual information. It assists in differentiating between alerts that may be less serious or have a smaller potential impact and those that are more likely to result in genuine security events. Organizations may deploy resources wisely and react quickly to the most serious security risks by prioritizing warnings based on context.
Risk scoring and risk analytics
Risk scoring and risk analytics are crucial to the prioritization of alerts. Risk scoring offers a standardized technique to evaluate the seriousness of hazards by quantifying their possible impact and likelihood. Organizations can efficiently prioritize alerts based on their risk score by giving each one a numerical number or score.
Beyond specific alerts, risk analytics offer perceptions into the environment’s trends and overall security posture. Organizations can spot trends, security holes, and areas for development by analyzing risk data. It enables security teams to focus on the most important areas of concern, manage resources effectively, and make educated decisions.
Leveraging risk scoring and analytics empowers organizations to take a proactive approach to security. By prioritizing alerts based on their risk scores and analyzing risk data, organizations can effectively address the most significant threats, strengthen their security posture, and minimize the potential impact of security incidents.
CheckRed: Your partner-in-security
CheckRed is a powerful SSPM and CSPM solution that supports effective alert prioritization, enabling organizations to swiftly address critical threats and reduce risks. Here is how CheckRed does it:
CheckRed’s prioritized alert capabilities
CheckRed’s platform categorizes and prioritizes alerts based on their severity and potential impact. It provides real-time visibility and offers a comprehensive view of the organization’s risk posture. Prioritized alerts enable swift detection and mitigation of critical threats, minimizing the window of vulnerability and reducing potential damages.
Collaboration and efficiency
Cross-functional collaboration: CheckRed emphasizes the importance of effective communication and collaboration between IT, security teams, and stakeholders. It integrates with popular communication tools such as Slack and Jira.
Streamlined incident response: CheckRed’s prioritized alerts streamline the incident response process by providing clear visibility and actionable insights. This streamlining enhances coordination, reduces response time, and minimizes the impact of security incidents.
Other relevant features
In addition to alert prioritization, CheckRed offers a comprehensive SSPM and CSPM platform. It includes features such as compliance monitoring, remediation workflows, and insightful reports to strengthen security posture and ensure regulatory compliance.
CheckRed empowers organizations to proactively protect their SaaS and cloud environments. With its comprehensive capabilities, CheckRed is the perfect partner-in-security that helps enhance security posture and assists organizations in achieving regulatory compliance.