Every October, Cybersecurity Awareness Month reminds us that vigilance isn’t just about protecting passwords or avoiding...
Compliance
7 Critical SaaS Security Lessons from the CHC Data Breach
In January 2025, Community Health Center (CHC), a nonprofit healthcare provider, discovered a data breach that compromised...
The Changing Face of Healthcare Cybersecurity: Updates to the HIPAA Security Rule
The healthcare industry is facing an unprecedented rise in cyberattacks, with breaches becoming increasingly frequent and...
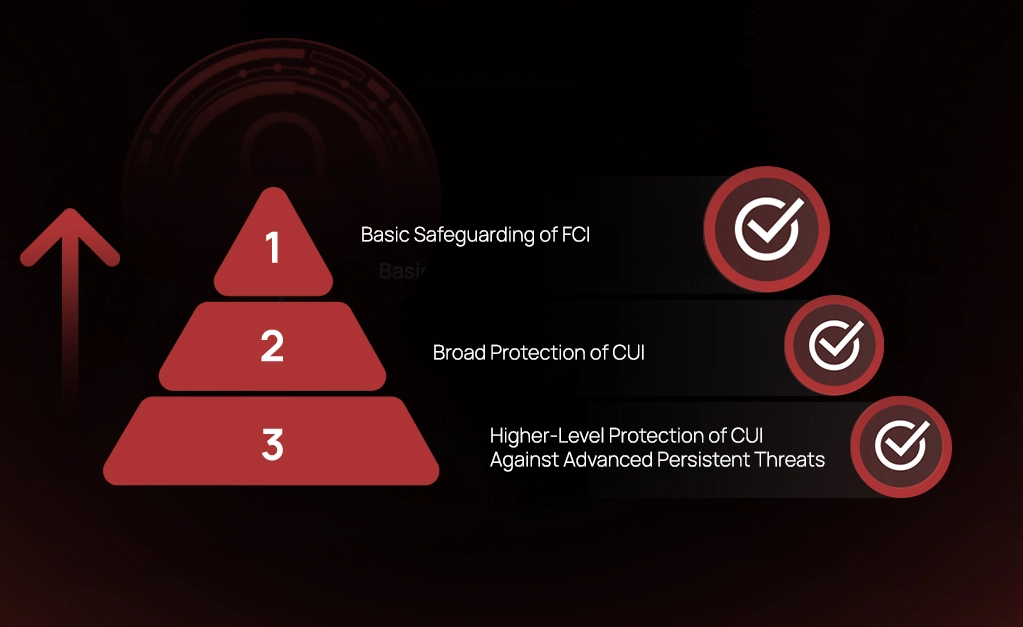
Understanding CMMC 2.0 – A Guide for MSPs and MSSPs
As an MSP or MSSP, helping your clients navigate the complexities of cybersecurity is a critical part of your...
Navigating the evolving cloud compliance landscape
Cloud compliance is undergoing rapid and continuous evolution. With the increasing reliance on cloud infrastructure,...
Digital Operational Resilience Act (DORA)
Understanding the Digital Operational Resilience Act (DORA) is important for cloud compliance, especially for organizations...
The Importance of CIEM for Financial Organizations
Financial organizations today face an ever-expanding variety of cybersecurity risks that threaten the integrity of their...
Mother of All Breaches – 26 Billion Records Leaked!
In January 2024, the cybersecurity domain witnessed a seismic event: the discovery of the "Mother of all Breaches" (MOAB)....
The impact of SEC regulations on MSPs and MSSPs
The Securities and Exchange Commission (SEC) has enacted a landmark cybersecurity disclosure rule. This new legislation...