In March 2025, a forgotten credential led to a very public incident. A threat actor known as “GHNA” published 270,000...
7 Critical SaaS Security Lessons from the CHC Data Breach
In January 2025, Community Health Center (CHC), a nonprofit healthcare provider, discovered a data breach that compromised...
Security Risks in Microsoft 365: Why Enterprises Are Taking a Closer Look Before Deploying at Scale
In a move that’s turning heads across the enterprise IT world, Amazon has paused its $1 billion Microsoft 365 rollout, just...
Understanding the Latest Analysis of FY23 Risk and Vulnerability Assessments from the CISA
The Cybersecurity and Infrastructure Security Agency (CISA) conducts Risk and Vulnerability Assessments (RVAs) for federal...
A little mistrust can be the right approach – The zero trust approach to security
Zero trust is a cybersecurity model that assumes no entity - whether inside or outside the network - should be trusted by...
Silos are adversely affecting your security culture
In cloud computing, security is an ongoing concern of a critical nature. It’s not just about having robust tools and...
Managing the SaaS and cloud permissions gap
Companies increasingly rely on cloud services and SaaS applications to operate efficiently. These platforms require...
NIST CSF 2.0 Revolutionizes Governance Model for SaaS Applications
Have you ever thought about the changing landscape of SaaS applications in the light of recent advancements? The NIST CSF...
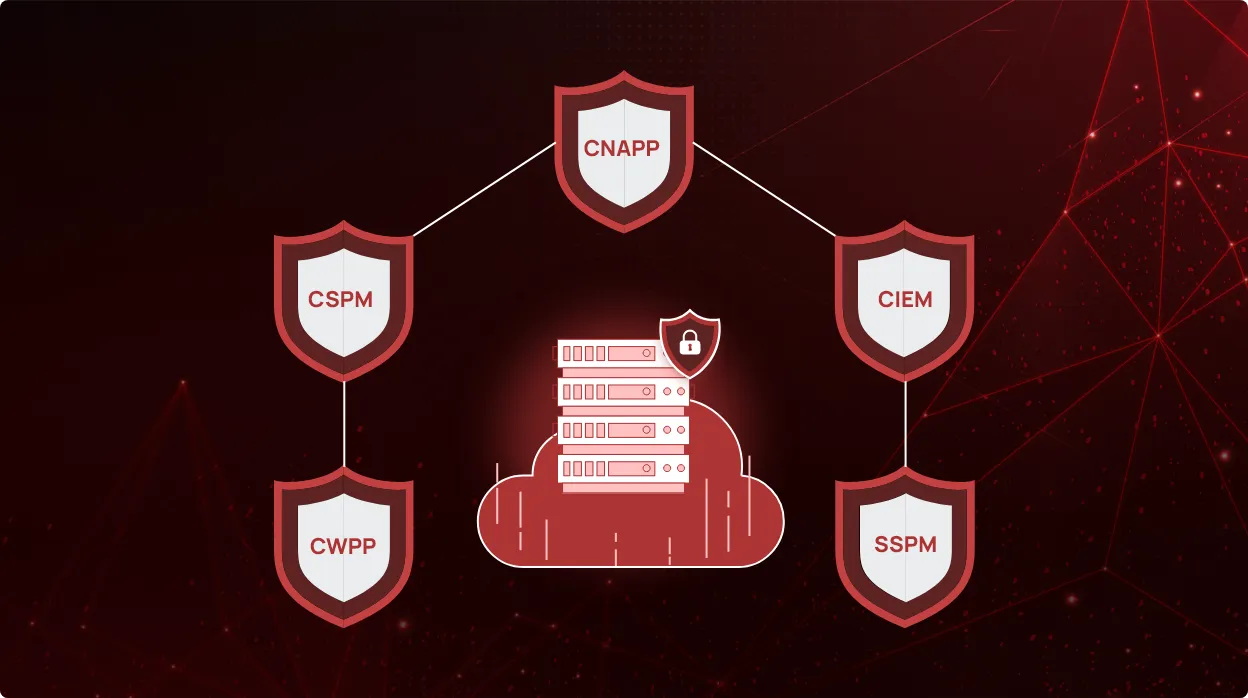
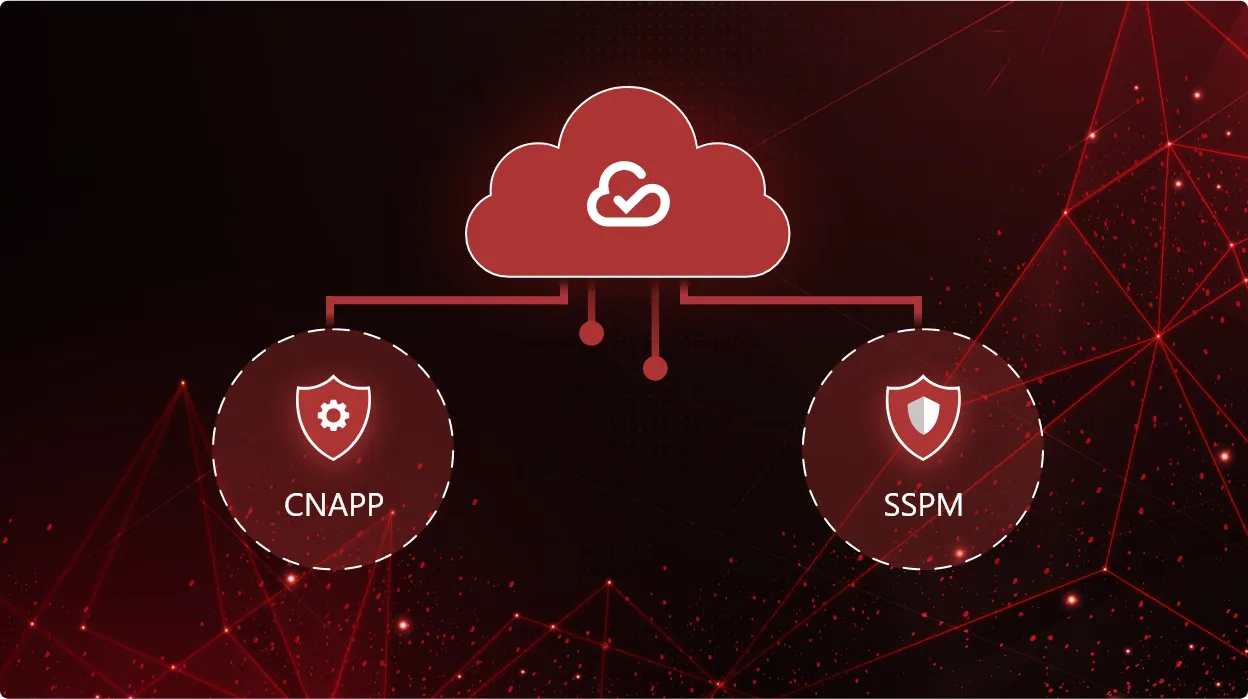
CheckRed extends platform capabilities to CNAPP and SSPM
CheckRed offers a powerful suite of cloud security solutions tailored to meet the evolving needs of modern enterprises. Our...