Kubernetes, often abbreviated as K8s, provides a robust platform for automating the deployment, scaling, and management of...
Introduction to Active Directory Posture Management
Active Directory (AD) is a critical component of any organization's IT infrastructure. Introduced by Microsoft over two...
Enhancing Cloud Security with MITRE ATT&CK: A Deep Dive into CheckRed’s Advanced Dashboard
In the rapidly evolving landscape of cybersecurity, understanding and mitigating threats requires a structured and...
Compensatory controls in cloud and SaaS environments
In cybersecurity, maintaining a strong defense is often hindered when standard security measures cannot be fully...
The Dropbox breach – Understanding the need for robust cloud security measures
In April 2024, Dropbox, a popular cloud storage service, disclosed a significant cybersecurity breach. Such cybersecurity...
Three major breaches that emphasize the need to manage third-party risk in the cloud
Today, organizations rely heavily on third-party vendors and service providers to streamline operations and enhance...
Exposure management in the cloud
Exposure management involves constantly scanning the horizon for potential threats and vulnerabilities. With the increasing...
Silos are adversely affecting your security culture
In cloud computing, security is an ongoing concern of a critical nature. It’s not just about having robust tools and...
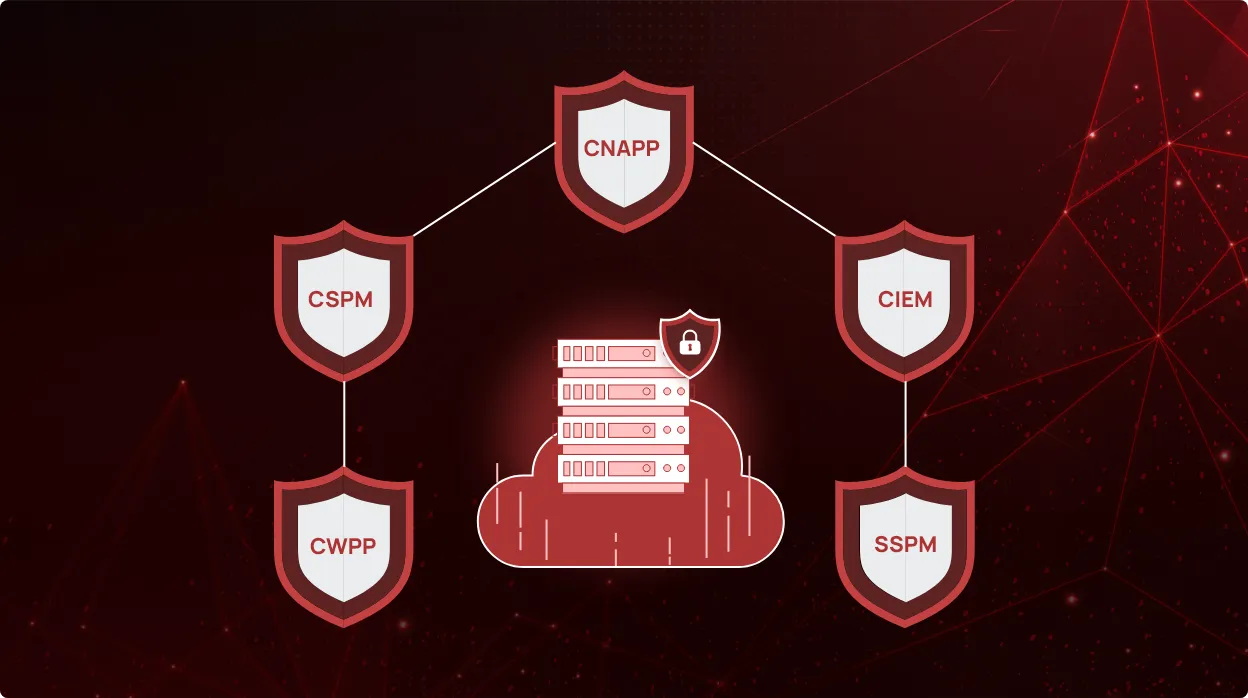
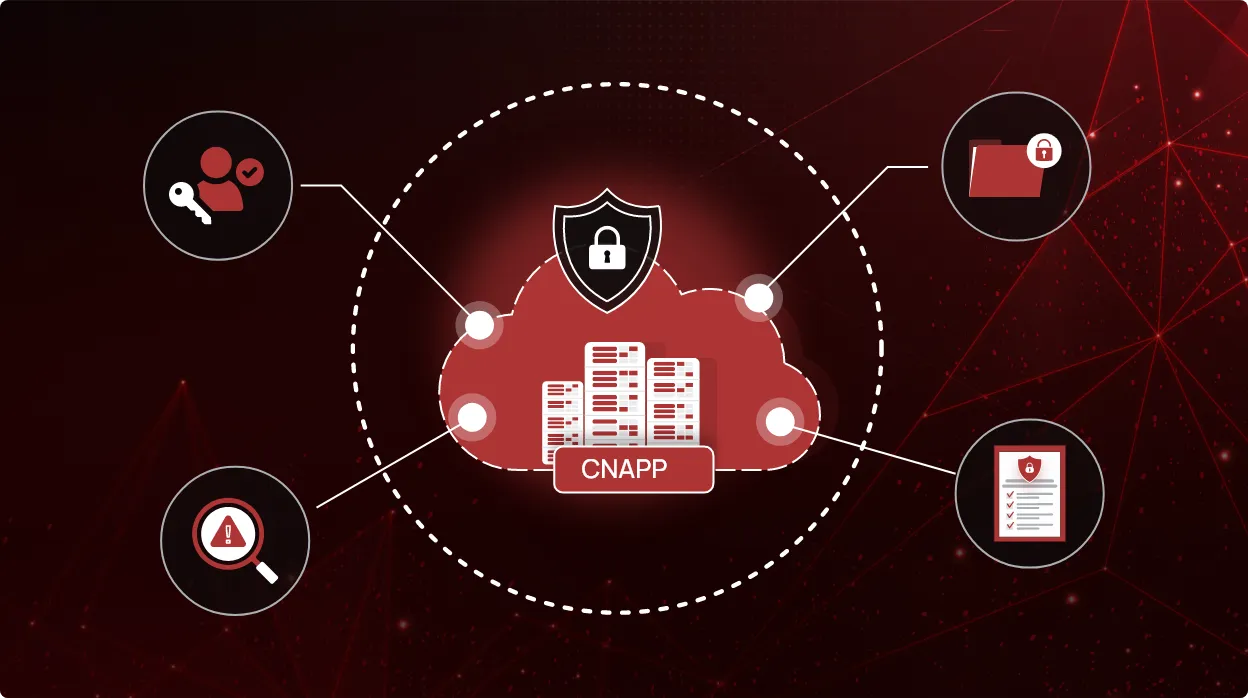
The rising importance of CNAPP
Cloud computing has transformed how organizations store, process, and manage their data. As more and more businesses...