Top Cloud Security Breaches: Lessons Learned from Notable Incidents

In our increasingly digital world, cloud computing has become the backbone of modern business operations. It offers scalability, flexibility, and cost-efficiency, making it an indispensable part of organizations across the globe. However, this digital transformation has also brought about new challenges, chief among them being cloud security.
Over the past few years, we have witnessed several high-profile cloud security breaches that have had far-reaching consequences. These incidents serve as reminders of the critical importance of robust cloud security measures. In this blog, we will explore some of the most significant cloud security breaches to date and the valuable lessons they offer.
SolarWinds Supply Chain Attack (2020)
The SolarWinds supply chain attack is often referred to as one of the most sophisticated cyberattacks in history. It began with attackers compromising the supply chain of SolarWinds, a trusted software provider widely used by organizations and government agencies. The attackers inserted a malicious update into SolarWinds’ Orion network management software, which was then distributed to customers.
Lessons Learned
- Supply Chain Vulnerability: This breach exposed the vulnerabilities in the software supply chain. Organizations must assess and monitor the security of their third-party vendors and suppliers.
- Continuous Monitoring: The attackers remained undetected for an extended period. Continuous monitoring and real-time threat detection are essential for identifying such intrusions promptly.
Capital One Data Breach (2019)
In 2019, Capital One fell victim to a significant data breach due to a misconfigured web application firewall. The breach exposed the personal data of over 100 million customers, including sensitive credit card information.
Lessons Learned:
- Secure Cloud Configuration: Properly configuring cloud resources and access controls is paramount. Misconfigurations can lead to severe data exposure.
Equifax Data Breach (2017)
One of the most infamous data breaches in history, the Equifax breach occurred due to the company’s failure to patch a known vulnerability in the Apache Struts software. This lapse resulted in the exposure of sensitive personal information for nearly 147 million individuals.
Lessons Learned:
- Patch Management: Timely patch management is non-negotiable. Organizations must have robust processes in place to identify and address vulnerabilities promptly.
JBS Ransomware Attack (2021)
In 2021, JBS, one of the world’s largest meat processing companies, experienced a ransomware attack that disrupted its operations across multiple countries. This incident underscored the potential impact of cyberattacks on critical infrastructure and global supply chains.
Lessons Learned:
- Incident Response: Having a well-defined incident response plan is crucial for minimizing the impact of ransomware attacks and ensuring business continuity.
Microsoft Exchange Server Vulnerabilities (2021)
Threat actors exploited multiple zero-day vulnerabilities in Microsoft Exchange Server to gain unauthorized access to email systems worldwide. This widespread attack had significant implications for organizations and governments.
Lessons Learned:
- Rapid Patching: Swift patching and vulnerability management are essential to prevent exploitation of known vulnerabilities.
Key Takeaways and Best Practices
These breaches offer essential lessons for organizations looking to enhance their cloud security posture:
- Supply Chain Security: Evaluate and monitor the security of your software and service providers to prevent supply chain attacks.
- Continuous Monitoring: Implement continuous monitoring and real-time threat detection to detect intrusions promptly.
- Secure Cloud Configuration: Ensure that cloud resources are configured correctly and access controls are in place to prevent misconfigurations.
- Patch Management: Establish robust patch management processes to keep software and systems up to date.
- Incident Response: Develop and regularly test an incident response plan to mitigate the impact of security incidents.
CheckRed solutions
Cloud Security Posture Management (CSPM)
At CheckRed, we understand the critical importance of cloud security and what misconfigured assets can result in. That’s why we offer cutting-edge Cloud Security Posture Management (CSPM) solutions. Our CSPM solutions provide real-time monitoring, threat detection, and actionable insights to help you secure your cloud environment effectively. With our expertise and technology, you can navigate the complex landscape of cloud security with confidence, knowing you are well-prepared to defend against the ever-evolving threat landscape.
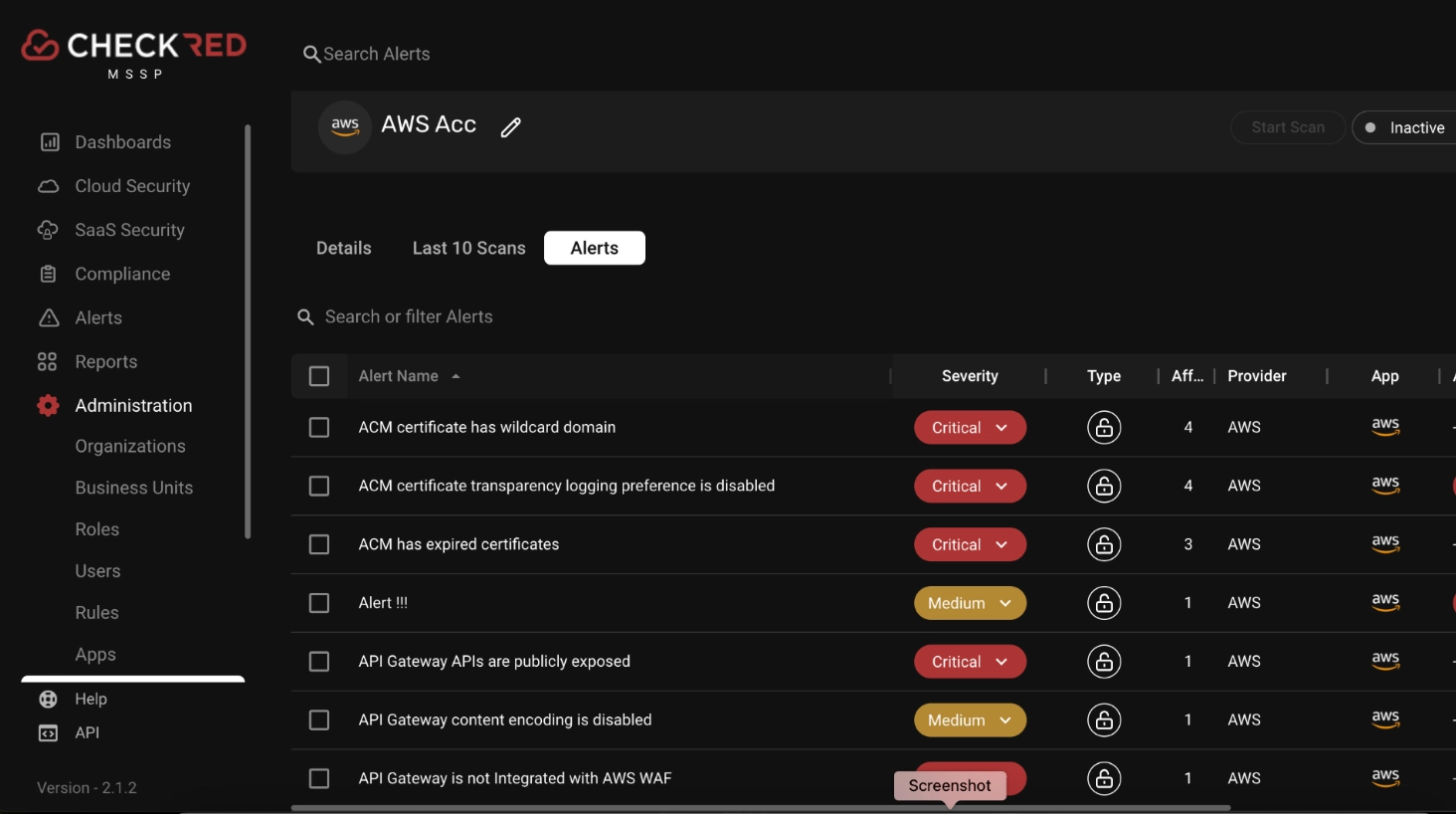
On board your cloud account in a few easy steps and discover misconfigurations in your environment. Here’s an alert view for an AWS account
Compliances
Compliance standards like NIST, ISO, HIPAA, and others are crucial for cloud security. They offer established security frameworks, risk mitigation, and data protection guidelines. By following recognized best practices, organizations can reduce security risks, ensure regulatory compliance, and protect sensitive data.
Check your compliance level now for your required compliance by running an assessment against your cloud account in minutes.
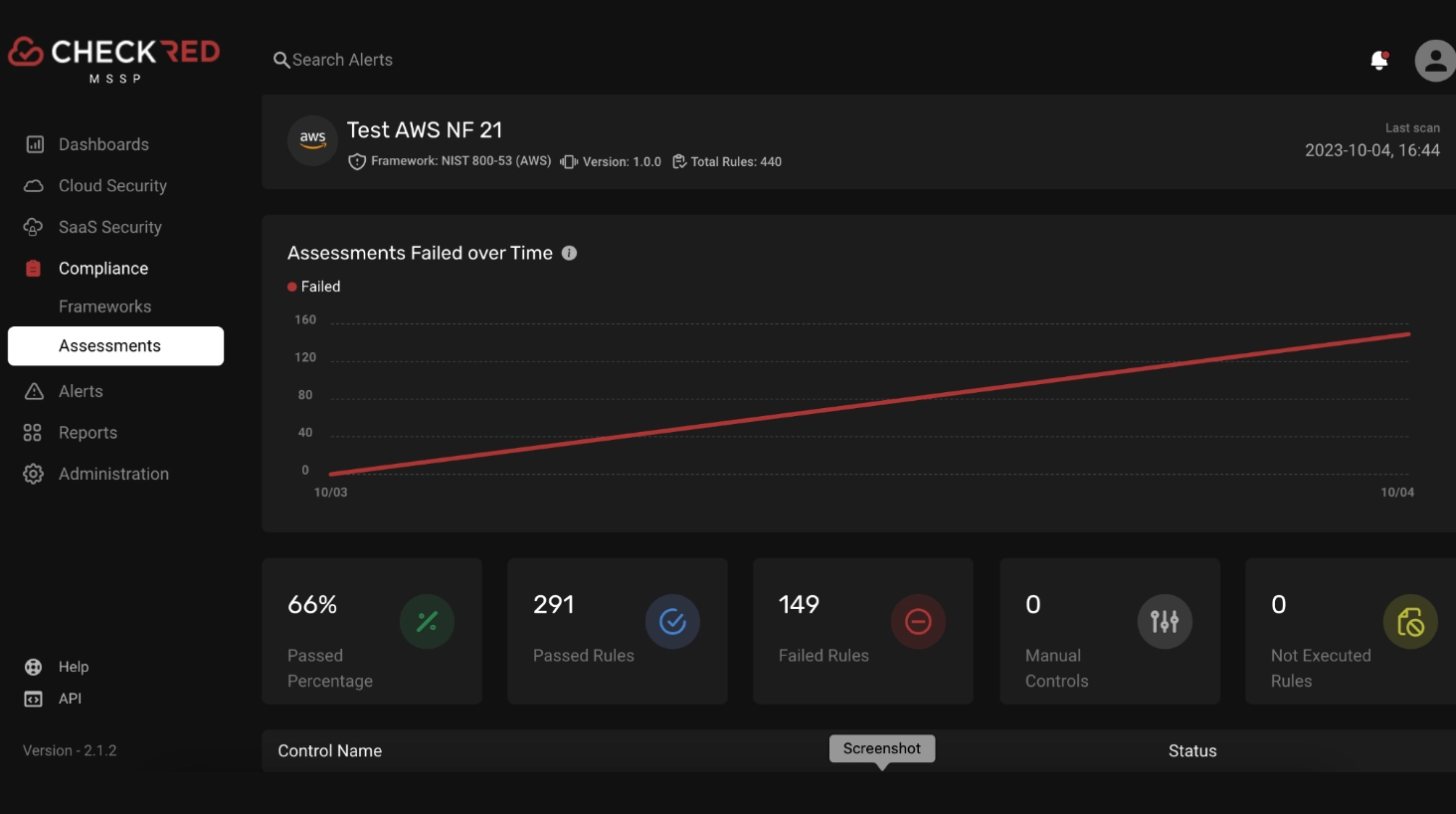
Here’s an example of NIST 800-53 assessment on an AWS account;
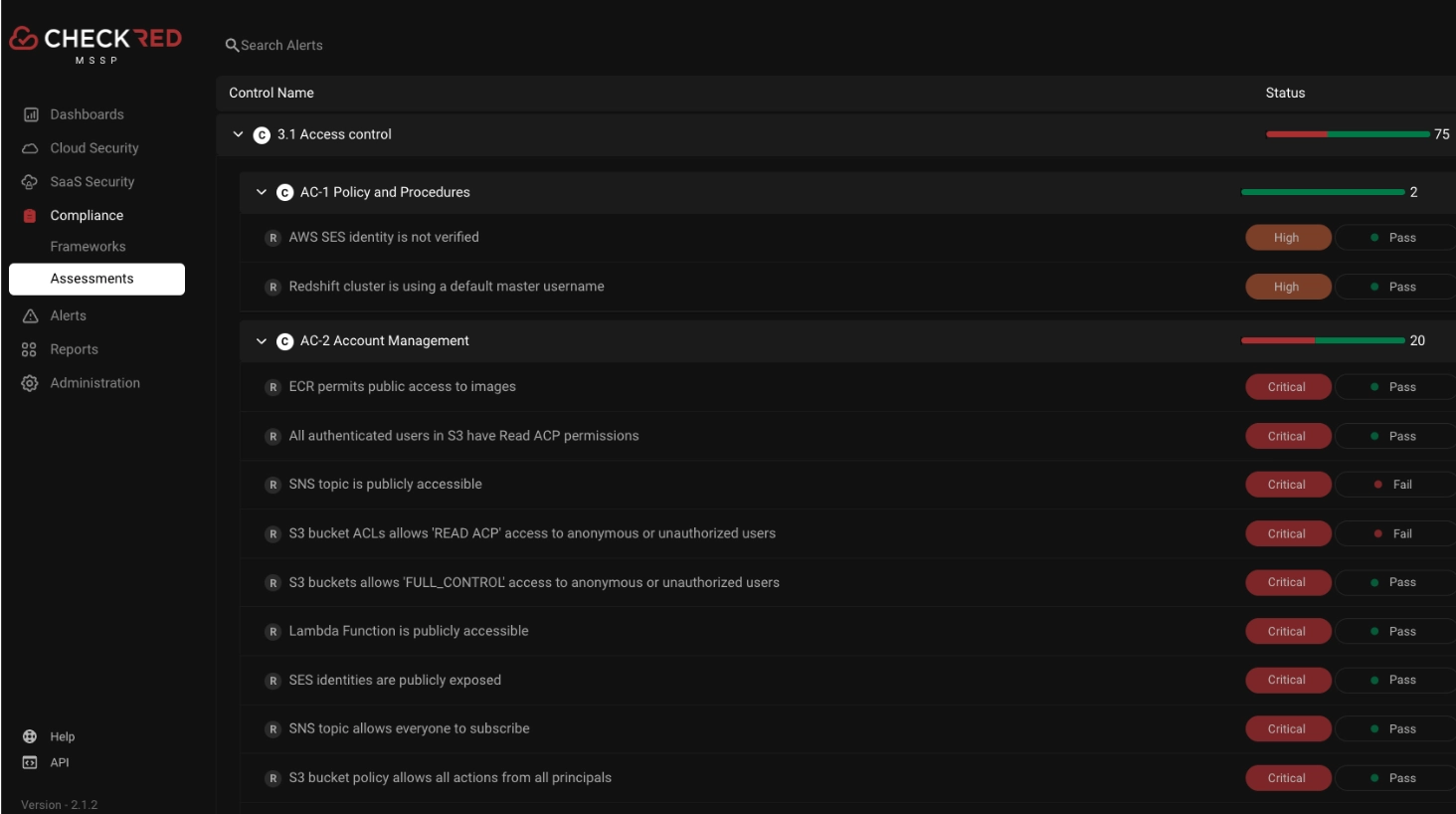
A more detailed view of controls triggering alerts;
Conclusion
The top cloud security breaches serve as stark reminders that no organization is immune to cyber threats. The importance of proactive cloud security measures cannot be overstated. By learning from these incidents and implementing best practices, organizations can better protect their digital assets and safeguard sensitive data.
Compliance frameworks such as NIST,ISO, HIPAA, and CIS Controls can provide valuable guidance and a structured approach to enhancing cloud security. These frameworks help organizations align their security practices with industry standards and regulatory requirements, further strengthening their defenses.